Law firms are prime targets for increasingly severe ransomware attacks. It’s time to take the threat more seriously.
NOTE: This article is intended to inform our readers about business-related concerns in the United States. It is in no way intended to provide legal advice or to endorse a specific course of action. For advice on your specific situation, consult your legal counsel.
Your law firm holds mountains of highly sensitive information including everything from client tax documents to company trade secrets. This makes you a prime target of ransomware attackers that are growing more aggressive by the day—and the scenario is more likely than you might think. Our recent survey found that a full third of law firms have been attacked in the last year.
In this report, we’ll reveal results from our recent law firm security survey, help you understand why the ransomware threat is growing so rapidly, and provide strategies to mitigate that risk to your practice.
What is ransomware?
Ransomware is a form of malware that encrypts data and prevents access to that data until a payment is made. Ransom payments are almost always made in the form of cryptocurrencies such as Bitcoin and Monero. Ransomware encrypts files using randomly generated symmetric and asymmetric keys. Upon payment of the ransom, the victim is sent the asymmetric key which is (hopefully) used to decrypt their files.
Law firm ransomware is a severe and rising threat
On June 4, the Biden administration compared the threat of modern ransomware to that of international terrorism and encouraged all businesses to take the threat much more seriously. This followed May’s attack on the Colonial Pipeline that led to gas shortages along the East Coast and a subsequent attack on JBS, the world’s largest meat producer.
Ransomware has been around since the late 1980s, but you might not have heard of it until 2017’s WannaCry attacks pushed the scheme into the global spotlight. In a matter of days, hundreds of thousands of WannaCry attacks unfolded across more than 150 countries, locking down everything from the U.K.’s National Health Service to Spain’s largest telecommunications company, Telefónica.
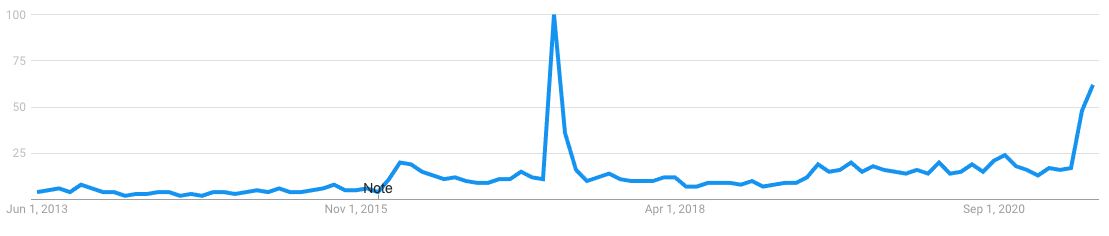
Eight years of Google Trends data for the search term ransomware. The big spike in 2017 is WannaCry—the recent spike began with May’s Colonial Pipeline attack. (Source)
But there was another severe—yet lesser known—ransomware strain in 2017 called NotPetya that caused more than $1.2 billion in global losses. NotPetya was an even more sophisticated threat than WannaCry, crippling countless major companies, including DLA Piper, one of the world’s top three law firms.
DLA Piper’s network was impacted for more than a week, leaving attorneys without access to client data, email, and even phone systems. In the end, the attack cost DLA Piper an estimated $300 million and required several months of remediation for the firm to become fully operational again.
If DLA Piper can’t prevent a ransomware attack, how well can small and midsize firms like yours expect to fare?
According to the law firms we surveyed, not so well.
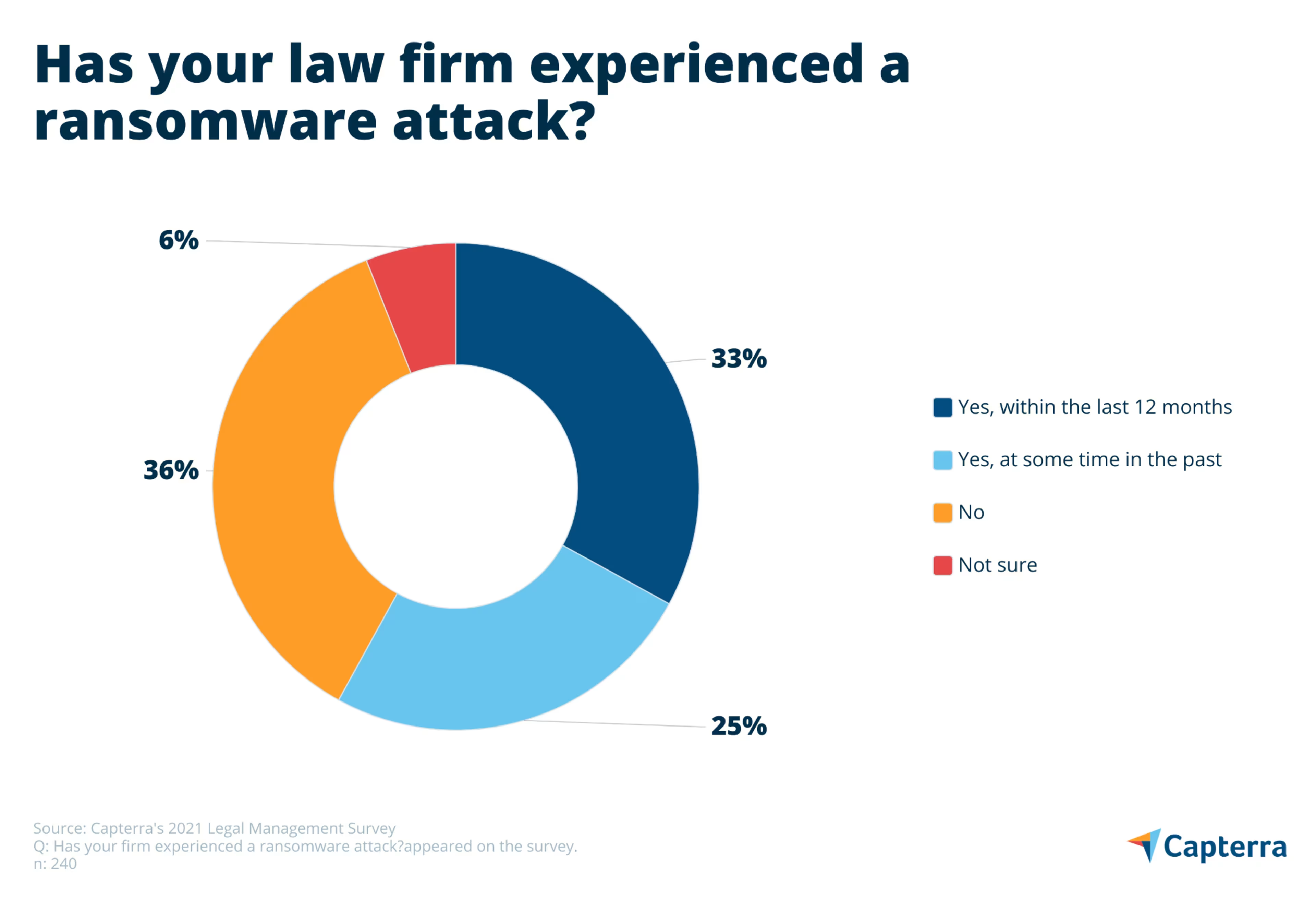
One in three law firms attacked by ransomware in last 12 months
Our research finds that 58% of small and midsize law firms have experienced a ransomware incident. More startlingly, our research finds that one in three (33%) have been attacked in just the last 12 months.
In contrast to autospreading ransomware strains such as WannaCry and NotPetya, newer human-operated ransomware variants such as Ryuk and REvil are increasingly aimed at specific organizations. They operate ransomware-as-a-service models which permit affiliates to launch attacks in exchange for a cut of the profits.
That’s why we've seen a sharp increase in highly-targeted ransomware attacks on entities known to possess valuable and time-sensitive data including hospitals, municipalities, and law firms. Ransomware gangs know full well that these organizations have little tolerance for downtime and are highly motivated to get operations back up and running as quickly as possible.
But it gets worse. Two-pronged ransomware attacks have now emerged that not only lock your data but also threaten to release a copy of the stolen files on the internet if the ransom isn’t paid—using a potential data breach to apply even more pressure.
Highly-targeted attacks are also resulting in astronomical ransom demands. A ransomware gang known as DarkSide (a REvil affiliate) collected nearly $5 million from the Colonial Pipeline attack while the JBS attackers pulled in a whopping $11 million. But even those sums pale in comparison to insurance giant CNA Financial’s shocking $40 million ransom payment back in March following a weeks-long ransomware attack.
How do law firms respond to a ransomware attack?
According to our survey, a full 69% of law firms pay the ransom. Of those firms that pay a ransom, about two in three (65%) are able to regain access to their data. But that also means 35% of firms pay a ransom only to get nothing in return.
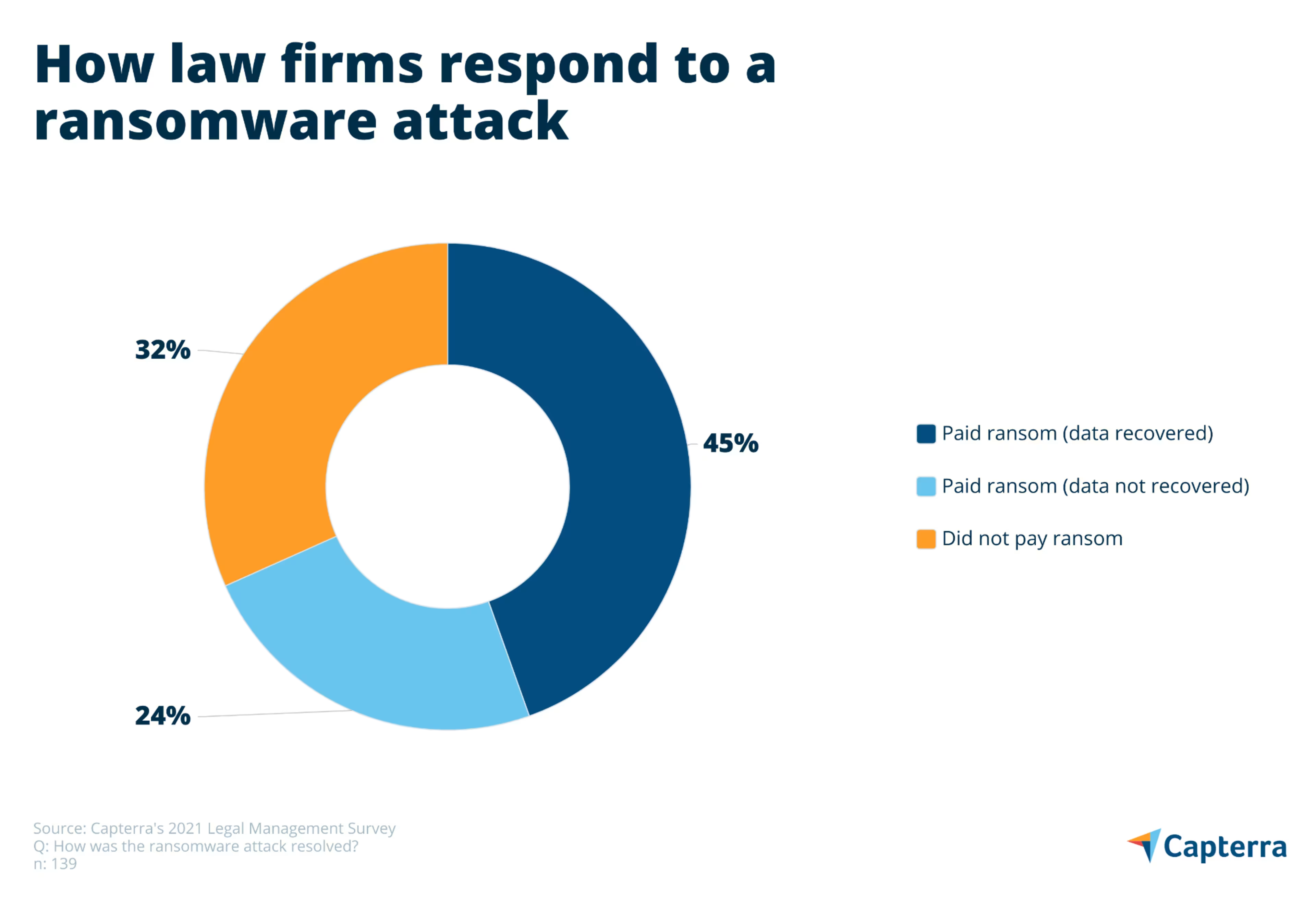
Of those law firms that refused to pay a ransom, 57% were able to decrypt or otherwise remove the malware. Another 32% of firms that didn’t pay were able to recover from the attack using a data backup, a key strategy for preventing a total data loss—a ransomware attack’s worst case scenario.
If you find that your firm has become a ransomware victim, contact your local FBI field office and report the incident to the Internet Crime Complaint Center (IC3).
You can also look to free resources such as ID Ransomware and the No More Ransomware Project to help figure out exactly what type of malware you’re dealing with and find a decryption key that might allow you to remove the ransomware without making a payment.
If all else fails, all law firms should have a strong data backup and restoration strategy to fall back on. If yours doesn’t, be sure to check out Capterra’s data backup software shortlist to find the tool that works best for your firm.
5 tips to protect your law firm against a ransomware attack
Some ransomware variants harvest network credentials while others enter your network via insecure ports or remote devices. But most ransomware infections stem from inadequate network security, phishing schemes, and poor employee security hygiene. Here are a few steps you can take to mitigate the threat of a ransomware attack on your firm.
Tip #1: Improve your security posture
Conduct a cybersecurity risk assessment to gain a full understanding of your firm’s information assets and identify security vulnerabilities that put them in peril. Some firms choose to go a step further and employ penetration testing (i.e., controlled hacking) to identify and correct network vulnerabilities.
Fortunately, 83% of the firms in our survey have conducted a security assessment of their digital systems at some time in the past—but only 39% have done so in the last year. The dynamic nature of cyberthreats demands that security assessments be carried out annually.
If you’d like to improve security but are not sure where to start, one option is to use the ISO/IEC 270001 framework to set a benchmark for your firm, whether or not you choose to go through with certification. The standards provided by ISO/IEC 270001 can help your firm identify security weaknesses and develop the policies and controls needed to protect it against cybersecurity threats.
Tip #2: Ensure that all software is updated
The WannaCry and NotPetya attacks leveraged the EternalBlue exploit to infect Windows devices that had not yet been patched. Frustratingly, Microsoft had made the patch available months before the first WannaCry attacks and any organization that had properly updated their systems would have easily avoided infection.
The simple lesson here is to ensure that all of your software is up to date at all times. Enable automatic updates on software that offers it and periodically check for updates on software that doesn’t. Keep in mind that your software might reach an end-of-life status after which it is no longer supported with updates. In these situations, you must upgrade to new software or replace your unsupported devices.
Tip #3: Use strong passwords and authentication methods
Use complex passwords or passphrases made up of at least 12 characters (always include numbers, uppercase letters, lowercase letters, and special characters) and be sure to use a unique password for each and every account. To make this easier, many firms opt for password management software that automatically creates strong passwords and stores them securely.
But passwords are not enough on their own. Ensure that two-factor authentication (2FA) is enabled for all business applications (i.e., require secondary security measures such as a code sent to your mobile phone). This is the single most effective way to prevent most of the methods cybercriminals use to compromise networks, takeover accounts, and ultimately install ransomware.
Unfortunately, only 54% of firms surveyed use 2FA for all business applications. This number is far too low and means that nearly half of all law firms are foolishly banking on passwords alone to protect their data. It’s worth noting that the Colonial Pipeline attack was the result of a single compromised password for a company VPN login that did not have two-factor authentication enabled.
Tip #4: Protect against phishing schemes
Phishing schemes remain a primary attack vector for ransomware attacks. In fact, the DLA Piper ransomware attack was traced back to the firm’s Ukraine office where an administrator clicked a link in a phishing email.
It’s critical that all law firm staff be up to date on the sophisticated phishing schemes that target individual employees and dupe them into clicking a malicious link, downloading a malware-laden attachment, or entering their credentials into a bogus website. Conduct phishing tests to determine your staff’s vulnerability to social engineering tactics and phishing schemes.
Our research finds that 52% of law firms rely on email as their primary means of internal communication. This means that protecting against email threats must be among your top priorities. Visit our email security catalog to find the best tool for your firm.
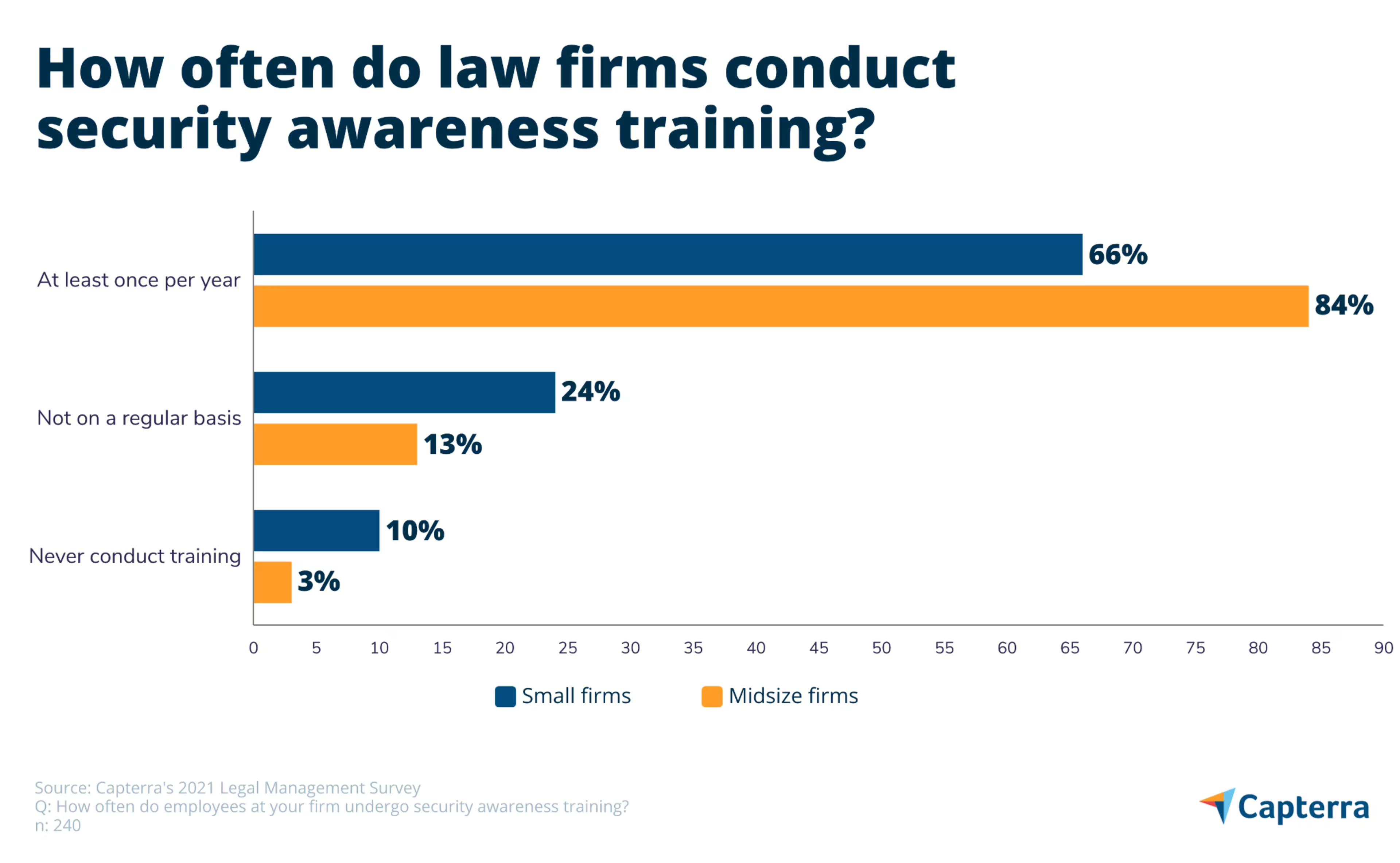
Tip #5: Conduct regular security awareness training
The key to preventing all types of cybersecurity threats is security awareness training. Our survey found that 75% of small and midsize firms conduct security awareness training on a regular basis.
And while three out of four isn’t bad, closer inspection finds that small firms are lagging well behind midsize firms. Only 65% of small firms conduct regular security awareness training compared to 84% of midsize firms. Moreover, an alarming 1 in 10 small firms say they never provide security awareness training.
If you need help getting started on an employee security awareness training program, take a look at our shortlist of the best training software platforms according to a collection of unbiased data and user reviews. If you only have a few employees, take a look at our list of free and open source learning management system (LMS) software to find low-cost training solutions.
An ounce of prevention is worth a pound of security
In 2018, the American Bar Association issued formal opinion 483 which expanded lawyers’ duty of competence to the secure use of technology and established an obligation to monitor for, and effectively respond to, data breaches.
This means that employing basic preventative measures to secure your firm’s data isn’t just best practice, it’s an obligation.
In the end, the decision to pay or not to pay a ransom is up to each firm and its unique circumstances. While our research finds that paying the ransom works more often than it doesn’t, making that payment incentivizes threat actors to continue their schemes and could also encourage subsequent attacks on your firm.
