Connected medical devices are expanding attack surfaces and making healthcare organizations more vulnerable to security threats.
The medical internet of things (IoT) is helping to make healthcare more convenient, efficient, and patient-focused. But it’s also endangering the security of healthcare facilities, and even patients themselves.
Capterra’s 2022 Medical IoT Survey [*] finds that healthcare organizations with more connected medical devices experience more cyberattacks—and about half of healthcare cyberattacks impact patient care.
Whether you’re a healthcare IT professional or simply concerned about the security of your practice, this report will leverage our survey results to help you understand how connected medical devices pose a threat to healthcare and what you can do about it.
/ Key findings
Healthcare organizations with a higher percentage of connected medical devices suffer more cyberattacks.
Nearly half (48%) of healthcare cyberattacks impact patient care, and two in three (67%) affect patient data.
More than half (53%) of healthcare IT staff view the current cybersecurity threat landscape as high or extreme.
Less than half (43%) of practices say they always change default passwords on connected medical devices, and less than a third (32%) always update them when a patch is available.
More connected devices, more problems for healthcare companies
A full three in four healthcare practices (75%) have experienced a cyberattack—41% of these practices have experienced multiple attacks.
Our research also finds that a plurality of healthcare organizations (40%) have between 51% and 70% of their medical devices connected to the internet, either through Wi-Fi or hardwired while a third (34%) have more than 70% connected. Only about a quarter of practices (26%) have half or less of their medical devices connected. Clearly, the medical IoT is no longer on the rise, but is now firmly entrenched at most healthcare organizations.
We wanted to find out if practices with higher percentages of medical devices connected to the internet experience higher rates of cyberattacks—and as it turns out, they do.
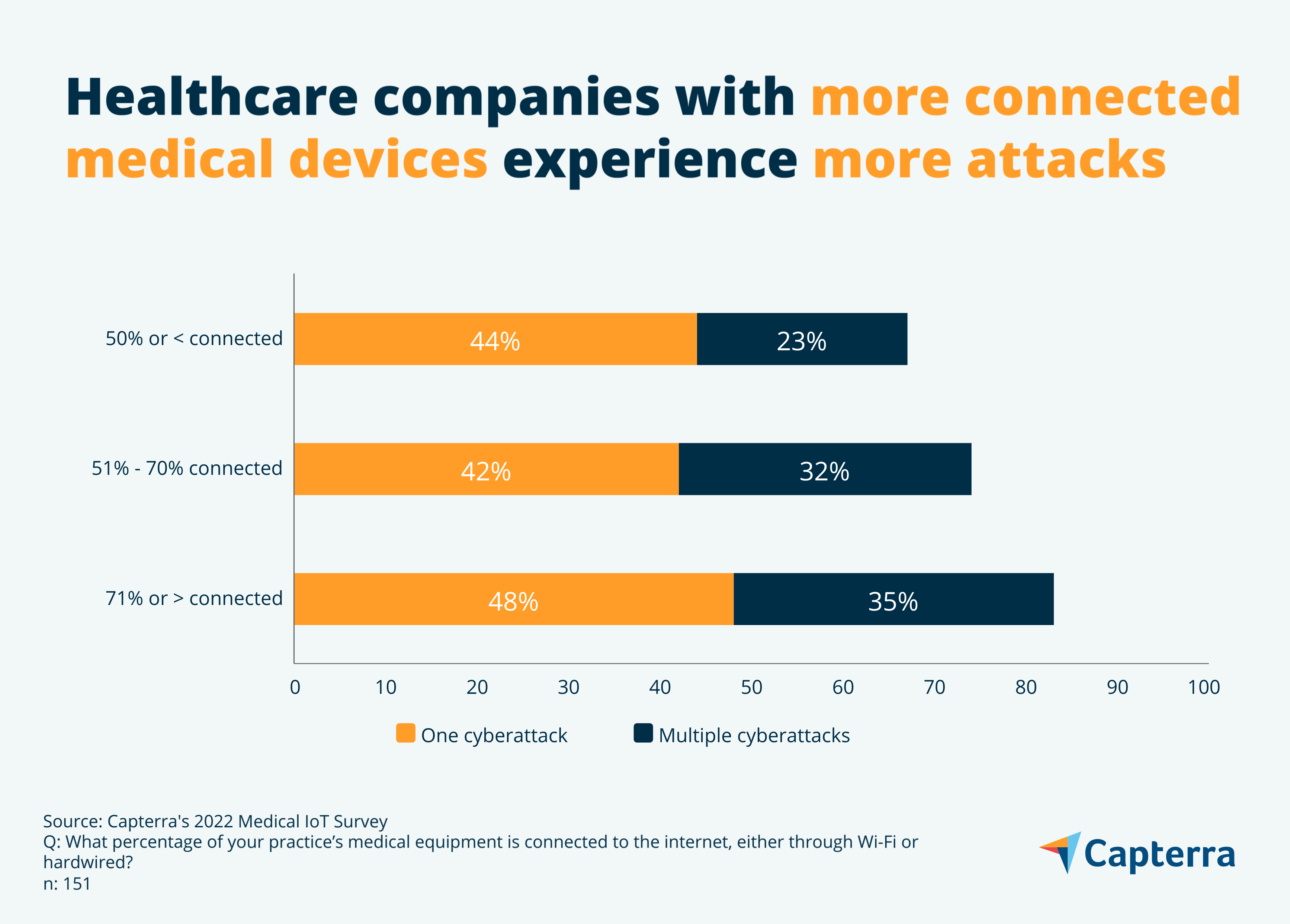
Practices with more than 70% of their devices connected are 24% more likely to experience a cyberattack than practices with 50% or fewer connected devices–and these highly-connected practices are 52% more likely to experience multiple cyberattacks.
This makes sense. As your healthcare organization connects more and more medical devices to its network, its attack surface expands. And because medical devices are typically developed with security as an afterthought, these new entry points into your network tend to be highly vulnerable and difficult to protect from attack. More on that later.
Nearly half of cyberattacks impact patient care
According to our survey, nearly half of healthcare cyberattacks (48%) affect patient care and two-thirds (67%) affect patient data. Only 10% do not impact either patient care or data.
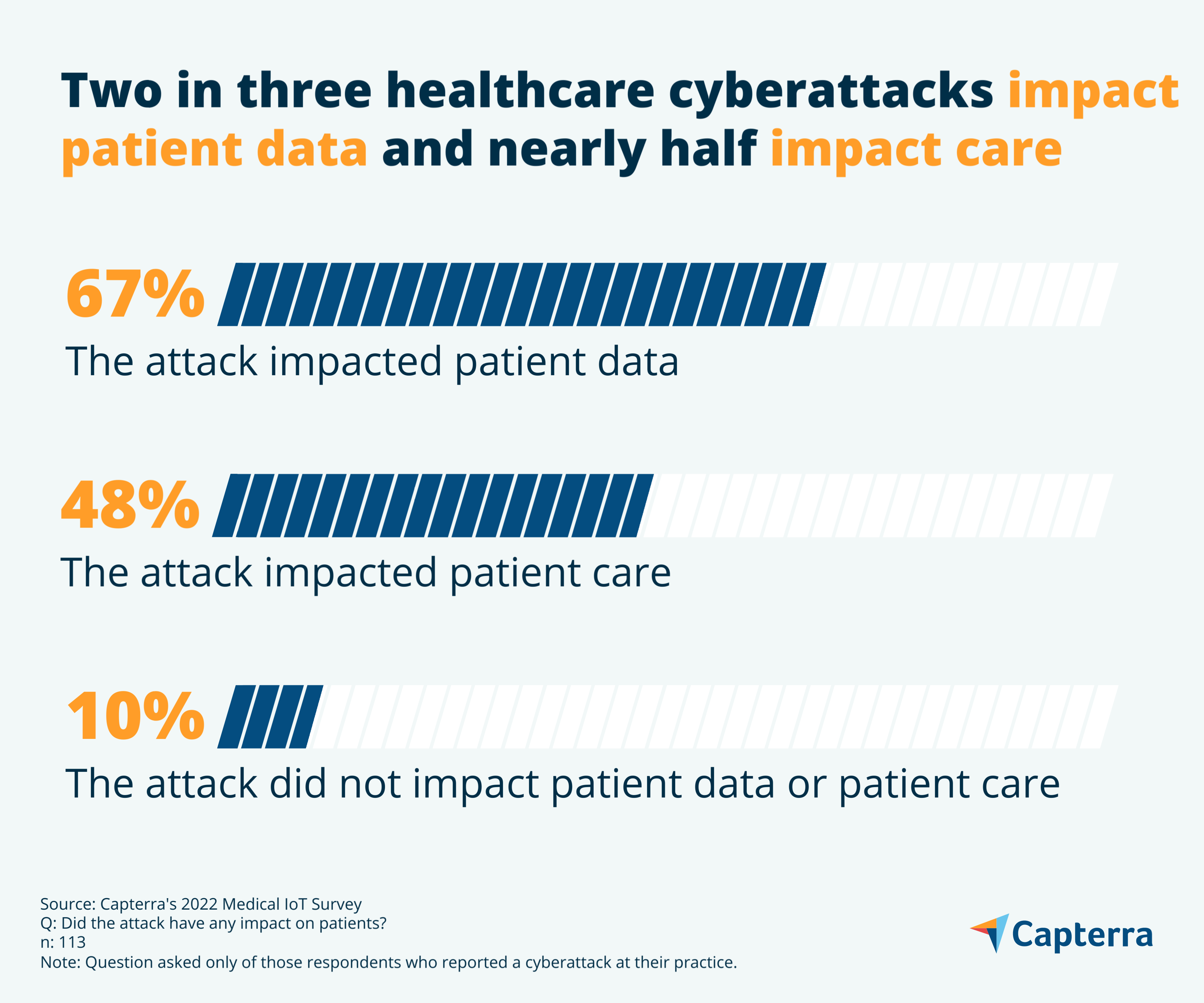
It’s common for cyberattacks to cause downtime and impact productivity no matter the industry—but when they hit healthcare providers, downtime means inaccessible health data, malfunctioning devices, and delayed procedures. In the worst case scenario, a cyberattack could even impact patient mortality, the subject of a pending lawsuit[1] that claims a hospital ransomware attack led to the death of a newborn, the first litigation of its kind.
Less grim but still concerning is the impact of cyberattacks on patient data. Beyond the obvious privacy implications for patients, this is a potential regulatory nightmare for practices that must safeguard protected health information (PHI) in accordance with HIPAA and HITECH regulations.
Researchers shine light on medical device vulnerabilities—but many healthcare IT staff remain in the dark
In the summer of 2017, WannaCry ransomware spread rapidly across the globe, affecting networks in 150 countries within days[2]. WannaCry (and later NotPetya ransomware) took advantage of the EternalBlue exploit, which allowed the self-replicating worm to spread quickly among vulnerable Windows systems, including countless machines hosting connected medical devices.
The attacks were so severe that the UK’s National Institute of Health temporarily suspended services and turned away patients at dozens of hospitals. Yet, ransomware attacks have only become more widespread in the years since WannaCry.
In 2019, a set of software bugs labeled Urgent/11 were found in the VXWorks software used in billions of devices and industrial systems across numerous industries including patient monitors and MRI machines (the two most used connected medical devices, according to our survey). Then, in 2020, researchers discovered the Ripple20 vulnerabilities which comprise a series of TCP/IP flaws in software used by medical devices, such as wireless infusion pumps.
EternalBlue, Urgent/11, and Ripple20 are only a few of the vulnerabilities known to affect connected medical devices but they are some of the most prominent and pervasive of recent years. Despite this, only about half of healthcare IT employees (54%) we surveyed consider themselves very familiar with Urgent/11, fewer (42%) say the same about EternalBlue, and only 38% feel well-versed on Ripple/20.
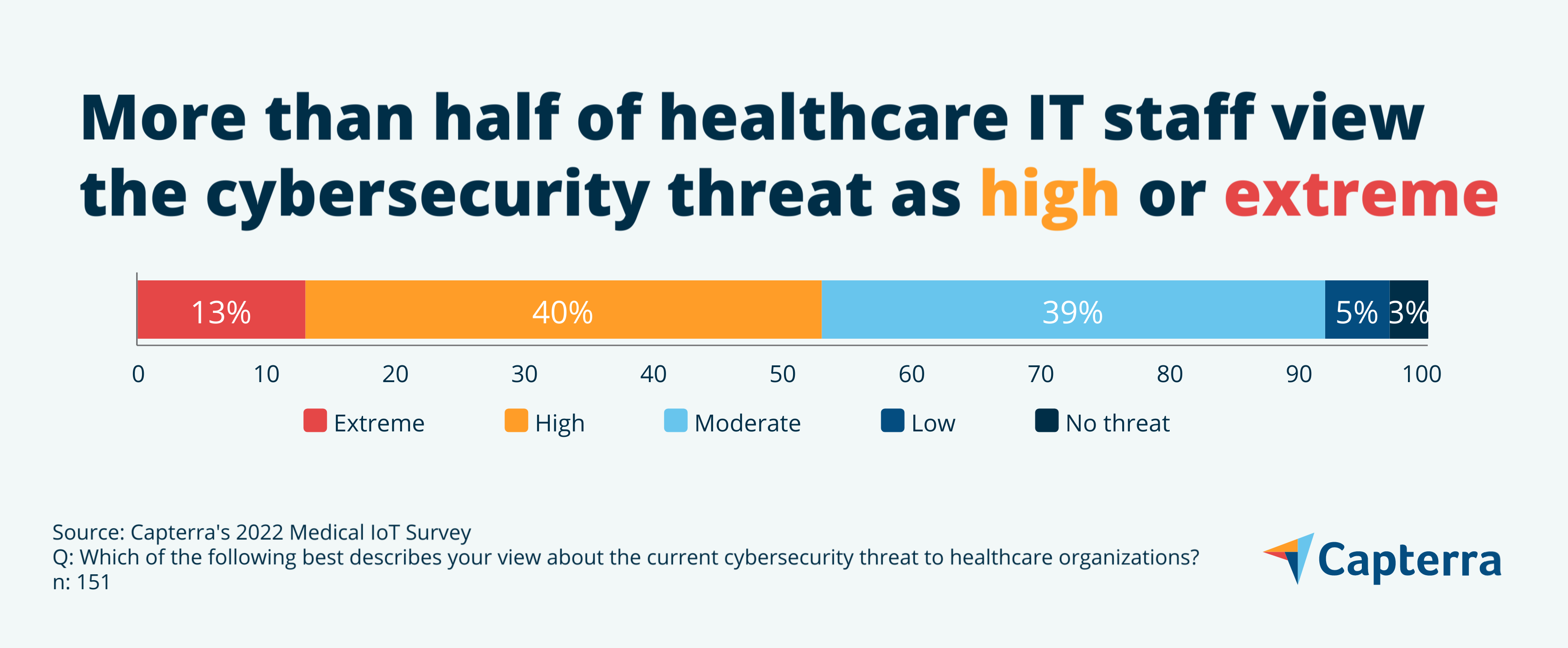
Rising risks to the healthcare sector, including sharp increases in ransomware, software supply chain attacks, and medical device vulnerabilities, mean healthcare IT staff are battling on multiple cybersecurity fronts. When asked their view on the healthcare sector’s current cybersecurity threat level, more than half of healthcare IT staff describe it as high or extreme.
Healthcare organizations are taking unnecessary risks with medical IoT devices
Before connecting any device to your network and putting it into use, you must change the default username and password. These default credentials are often easy to obtain by bad actors and make devices discoverable by search engines, such as Shodan. Alarmingly, 57% of healthcare IT employees say that they do not always change the default username and password for each new connected medical device that is put into use—including 5% who say they never do.
Once connected, medical devices often go unmonitored because they lack the ability to run solutions such as antivirus or endpoint protection tools that are typically used for desktop computers and other traditional network devices. In addition, IoT devices run on a wide array of software and hardware platforms that makes them difficult to monitor with a single tool. These factors mean that many connected medical devices are left wide open to cyber attacks.
Devices that do use traditional operating systems commonly run on legacy platforms that are no longer supported and cannot be patched. A full 82% of our respondents say that at least some of the connected medical devices at their practice run on Windows operating systems older than Windows 10.
If a vulnerability is discovered, the primary way to remedy the situation is to patch the device or update its firmware as soon as possible. Take EternalBlue: Microsoft had issued a patch months before WannaCry became a crisis and any systems that had been updated were protected. Unfortunately, two-thirds of practices (68%) tell us they do not always update connected medical devices when a patch is available.
It’s important to note that updating IoT devices isn’t always easy, or even possible. Would you know how to update the firmware on your smart refrigerator? Moreover, vulnerabilities and associated patches aren’t always well publicized, which means healthcare IT staff must stay up to date on emerging threats to medical IoT devices.

Medical IoT security requires proactive and ongoing vigilance
As mentioned, some of the key practices for securing medical IoT devices include changing default credentials, ensuring all operating systems are up to date, and applying patches as soon as possible. But these precautions are only the start; here are additional measures that will improve medical IoT security:
Maintain an up-to-date, complete, and accurate inventory of all connected medical devices and associated software or firmware including information, such as vendor, operating system, model number, and dates of service.
Conduct routine vulnerability assessments and scans before installing or reconnecting medical devices to your IT network.
Use IoT management software to monitor and protect applicable connected medical devices—explore our IoT software catalog and read our buyers guide to learn more.
Deploy network segmentation strategies by creating virtual local area networks (VLANs) to separate different types of devices and data flows to ensure you don’t have all of your network in one basket, thus reducing overall risk.
Focus on developing strong network access policies and adopt zero-trust strategies when available. For information on zero-trust security adoption, read our recent guide: Zero Trust Improves Cybersecurity According to 99% of Companies That Adopt It.
