Software supply chain vulnerabilities are opening companies up to new and insidious vulnerabilities—here’s what they can do about it.
It’s often been said that employees are the weakest link in your security chain—but our latest research suggests the weakest link might be somewhere in your software supply chain. Capterra’s 2023 Software Supply Chain Survey* finds that 61% of companies have been impacted by a supply chain attack in the last 12 months.
In this report, we’ll explore more of our survey results, put software supply chain attacks into perspective, and help business leaders such as yourself take steps to mitigate their impact.
What is a software supply chain attack?
A software supply chain attack occurs when someone infiltrates your network through a vulnerability in a third-party software platform. The mass adoption of cloud-based software has expanded attack surfaces, allowing threat actors to leverage supply chain vulnerabilities to gain access to (and launch attacks against) networks on a large scale. The consequences of these software vulnerabilities run the gamut from mass ransomware infections to attacks on critical infrastructure.
/ Key findings
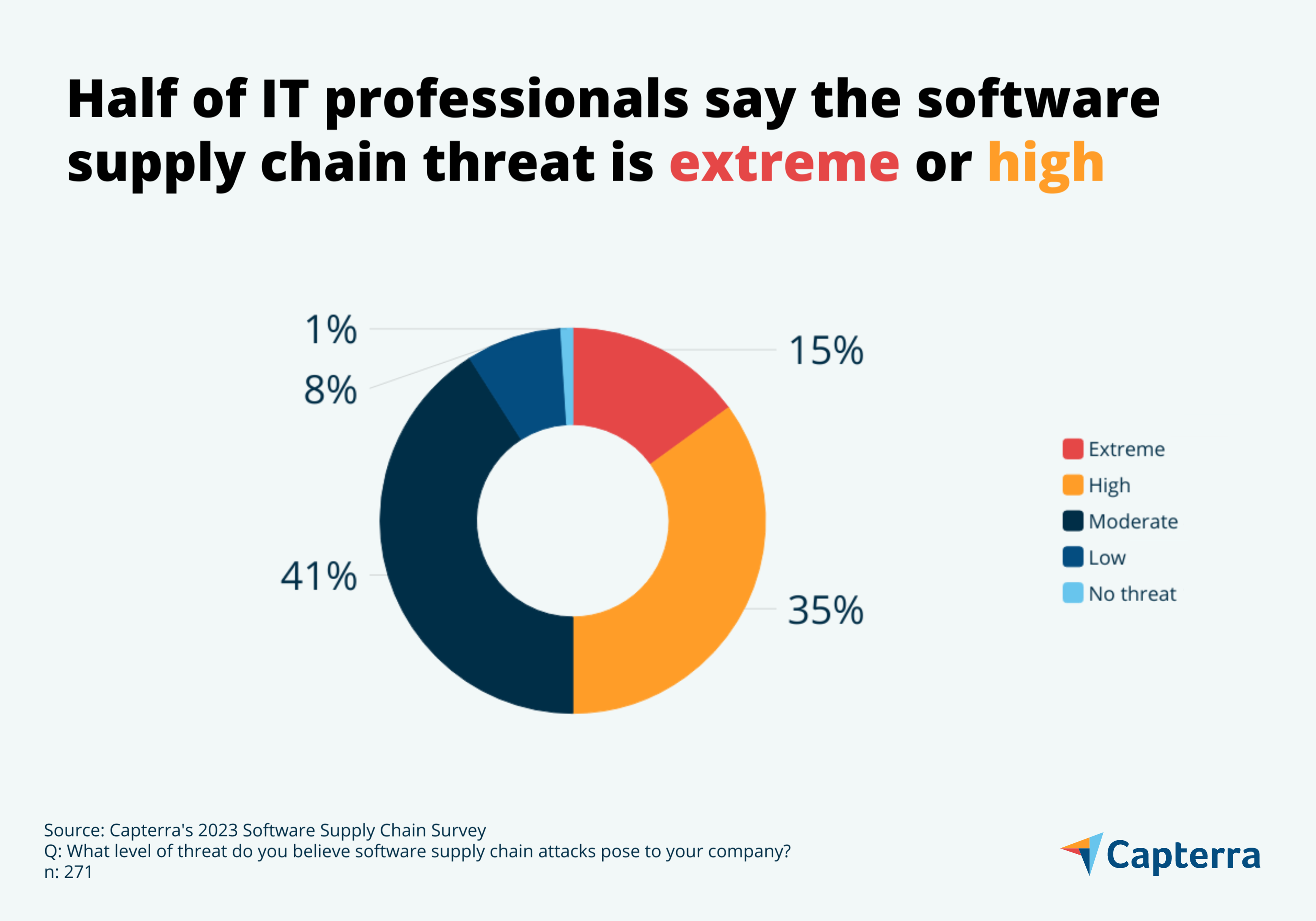
Half of the IT professionals surveyed say the software supply chain threat is high or extreme—another 41% say the risk is moderate and only 8% say it’s low.
Nearly all companies (94%) use at least one open source software platform and more than half (57%) use multiple.
App sprawl is associated with higher risk of software supply chain risks.
A majority of businesses conduct formal risk assessments (64%) and practice privileged access management (61%) to boost defenses against supply chain threats.
Software supply chain threats rising—61% of businesses impacted in last year
Supply chain attacks didn’t begin in December 2020, but that month’s SolarWinds hack put them firmly on the map for businesses around the world. Hackers had gained access to SolarWinds’ Orion IT Management platform months in advance and installed backdoors to launch subsequent attacks on dozens of the vendor’s clients, including NASA and the U.S. State Department[1]. All told, about 18,000 clients were required to update their systems to protect against attack.
One year later, a vulnerability was discovered in Apache’s Log4j logging library, a ubiquitous and open source program used in millions of software packages[2]. This time, the software supply chain threat was everywhere with millions of systems and devices vulnerable to malicious code injection. In the time since, more and more supply chain attacks have come to light, prompting congressional legislation and executive orders[3].
Our research shows that 61% of businesses have been affected by a supply chain threat in the last year, validating growing concerns and justifying a strong response from both businesses and the government. And if your company is one of the lucky 39% that made it through the last year unscathed, it’s likely luck more than anything. That’s because the vulnerabilities wrought by software supply chain vulnerabilities are difficult to defend against.
IT professionals sound the alarm—half say threat is high or extreme
The fact is that every single business that uses software is vulnerable to these attacks, at least to some extent. So the question isn’t if companies are vulnerable, it’s how vulnerable are they?
Exactly half of IT professionals believe that the threat posed by software supply chain attacks is high or extreme while another 41% say the threat is moderate—a mere 8% say the threat is low.
Open source software magnifies the supply chain threat
Software that is open source includes permission for use and distribution along with its source code being made available to the public. Examples of open source software include Linux, MondoDB, WordPress, and the aforementioned Apache Log4j. And while the rise of open source software (OSS) platforms and components have democratized and streamlined software development, it has also brought about vulnerabilities that can be exploited by bad actors.
This is a concern because a full 94% of companies use at least one fully open source software platform—57% use multiple. And those numbers are likely only the beginning. Most software platforms that are not fully open source include a lot of open source packages that developers leverage to speed up production.
Concern about OSS is one of many reasons for the rising demand among companies and government agencies for vendors to provide a software bill of materials (SBOM). An SBOM is an inventory of metadata that identifies and tracks the components used to build a software package. It’s meant to inform organizations so that security and compliance risks are better understood as they emerge.
Our research finds that about half (49%) of businesses request an SBOM from vendors as part of their defense strategy for software supply chain threats.
App sprawl worsens supply chain vulnerabilities
App sprawl occurs when your company continually adopts new software without getting rid of unused, overlapping, or redundant applications—a situation that afflicts more than half of U.S. retailers (55%), according to Capterra’s 2023 Retail App Sprawl Survey**.
When you think about app sprawl in relation to software supply chain attacks, one conclusion that you could easily draw is that the more apps you have, the more vulnerable you are. Our research suggests you’d be right.
Retailers that have experienced a cyberattack in the last two years are more than twice as likely to report being impacted by app sprawl (53% compared to 22%) as those that did not experience a cyberattack.
This finding strongly suggests a connection between excessive applications and the odds of experiencing a cyberattack that could in many cases be caused by a software supply chain vulnerability. It makes sense, then, that tackling app sprawl is a clear strategy to reduce the odds of falling prey to a software supply chain attack.
How to mitigate the software supply chain threat
Notice we said mitigate rather than prevent. The key to software supply chain risk is reducing the impact if—and most likely when—one occurs. In addition to reducing app sprawl and requesting an SBOM as mentioned above, here are a few other methods companies use to mitigate supply chain risks.
Formal risk assessments are conducted by 64% of businesses
Risk assessments are essential tools for gauging an organization’s ability to protect its assets from cyber threats. It’s important to understand the highest risks to your most critical data and systems to ensure that security resources are prioritized for these areas. In regard to software supply chain threats, risk assessments can identify the interconnected dependencies of software and inform risk tolerance for software purchases.
Privileged access management is practiced by 61% of businesses
Employees (or machines) with highly-privileged or admin access to data and systems are a top target for attackers. That’s because their elevated access allows them to bypass standard controls to make changes to IT or digital systems. Privileged access management is a strategy companies use to control the use of these accounts and ensure appropriate access to critical systems.
/ Recommended tools
Check out our Privileged Access Management catalog to find tools that can help your business better manage risks to critical systems and data.
Honeypots are deployed by 32% of businesses
Honeypots (or honeytokens) are virtual decoys that organizations use to catch an attacker before they are able to access legitimate systems and data. This strategy alerts organizations in advance to an attacker within their network, potentially limiting a supply chain attack’s impact.
In the end, software supply chain threats are a risk to your company if you use software. If that sounds like you, the best plan of action is to tighten your security controls and aim to reduce potential impacts.
To learn more about how to protect your business from software supply chain and other threats, read our recent report: Zero Trust Improves Cybersecurity According to 99% of Companies That Adopt It