Manage data breaches and mitigate loss with a cybersecurity incident response plan.
The escalating cost of dealing with cyberattacks can be crippling for small and midsize businesses (SMBs), especially if they don’t have the right detection and recovery plan.
The financial impact of cyber-physical system (CPS) attacks on businesses is expected to cross $50 billion by 2023, per Gartner research. This cost includes insurance, litigation, compensation, regulatory fines, and reputation loss. Gartner also predicts that by 2025, 75% of chief executive officers (CEOs) will be personally liable for CPS incidents.
To this end, having a cybersecurity incident response plan will help your small business accurately monitor systems, detect any security incident, and implement prevention or recovery methods to mitigate loss.
In this article, we explain how to create a cybersecurity incident response plan in five steps. But before we get into the details, let’s start by understanding what a cyber incident response plan is and why you should have one for your small business.
What is a cybersecurity incident response plan?
A cybersecurity incident response plan is a documented set of instructions that help businesses quickly and efficiently detect cyberattacks, isolate any affected system or network (in response to the attack), and recover from the resultant loss.
Since a cyber attack can affect your organization across functions, the plan you design should account for all functions and departments, including human resources, finance, customer service, legal, supply chain, employee communications, and business operations.
Find providers that can help with your business needs by using our lists of IT services agencies by location.

Here’s a quick comparison between two businesses with and without a cybersecurity incident response process. While both are compromised by the same attack, business B could reduce the impact due to proper planning.
Business A (Does not have a CIRP) | Business B (Has a CIRP) |
|---|---|
Detects a security incident but not sure how to respond. | Detects a security incident along with its type. |
Takes several hours to prepare a detailed report for declaration. | Quickly declares the incident after confirming with the chief information security officer and incident response experts. |
Since incident identification and declaration took time, the security breach spread to other business processes besides the initially impacted system. | Immediately isolates the affected system, user, and object from the rest of the business processes. |
No forensic partner to gather evidence for the legal team and advice on recovery. | Calls the forensic partner to gather evidence of the attack and advice on recovery. |
Recovery could not happen due to lack of evidence, resulting in loss. | Timely recovery saved the business from loss. |
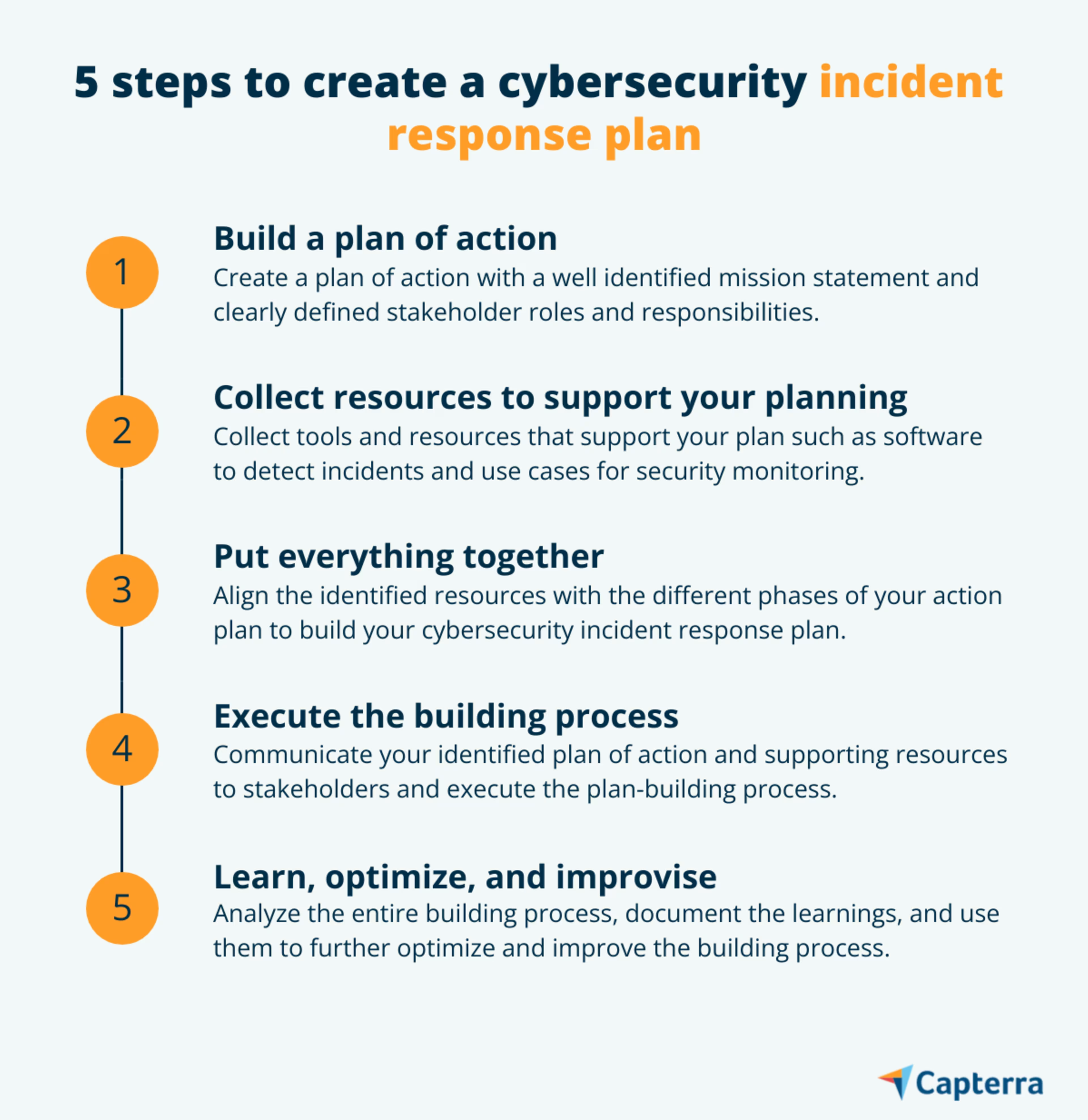
Step #1: Build a plan of action
Building a plan of action is the workhorse of the entire incident response planning process. The plan document should have the following elements:
A mission statement
A mission statement clearly defines the purpose of the incident response planning process, enabling you and other stakeholders to understand the scope of the work being done. As each of the stakeholders involved in the planning process may not be security and risk experts, the mission statement—with terms and definitions explained—will help them stay on the same page and take crucial decisions when required.
Here are a few examples of mission statements:
Defend against cybersecurity threats
Build an incident response team
Investigate cyberattacks and their types, and declare their impact on the business
Gather evidence of the attack and work with law enforcement to check if any legal regulations are impacted
Defined roles and responsibilities
Clearly defining stakeholder roles and responsibilities will make the planning process highly prospective—everyone will have a direction to work, and there will be no confusion. You can define roles and responsibilities by creating a driver, accountable, consulted, and informed (DACI) chart.
A DACI chart—also known as a RACI chart—defines which stakeholder is involved at which stage and what they are expected to do. It serves as a visual representation of the functional role each stakeholder plays. Here’s a free DACI template to get you started.
D - Driver | Individuals driving a task (e.g., CISO) |
|---|---|
A - Accountable | Individuals accountable for the success of the task (e.g., project manager) |
C - Consulted | Individuals who need to be consulted for information or affirmation (e.g., subject matter experts) |
I - Informed | Individuals who need to be informed about the task’s progress and updates (e.g., leadership). |
Step #2: Collect resources to support your planning
Once you’ve aced planning, the next step is to collect tools and resources to support your plan. For instance, if you identify data exfiltrationA few essentials to ensure you’re equipped with the right resources are:
Use cases for security monitoring
Security monitoring forms the base of implementing your plan on time and detecting incidents accurately, making it a crucial step in the process. Studying use cases—live examples of incident monitoring methods previously used within the business—and implementing the proven methods in your current monitoring process will not just increase your risk tolerance but also help plan response objectives.
Detecting security issues
Finding the right resources to detect and fix security issues across business functions is as important as having use cases. You can use incident management software to record, report, and prioritize various IT-related incidents, from data security breaches to system malfunctions. The software assigns tickets to IT personnel and sends notifications to stakeholders as soon as an issue arises to keep downtime to a minimum.
Step #3: Put things together
The next step is putting together all the hard work you’ve done until now in planning and collecting resources. The bulk of your efforts in this step goes into scoping and understanding the collected data and aligning it with the different phases of the prepared action plan. The goal is to check your team’s readiness to start building a security incident response plan.
Pro tip: Ensure each team member involved in building the cybersecurity incident response plan should have the skills and knowledge to understand live system responses, digital forensics, threat intelligence, and memory and malware analysis.
Step #4: Execute the building process
Once everything is in place, you’re all set to start building your cybersecurity incident response plan. Ensure the identified plan and resources are well communicated to your incident response team members and other stakeholders. This will help reduce the impact of a security incident.

Step #5: Learn, optimize, and improvise
Now that you’ve built your cybersecurity incident response plan, it’s time to analyze the entire building process, document the learnings—both mistakes and success—and use them to further optimize and improve the building process. The optimization could be anything from using a different set of resources to involving additional team members in the plan-building process. However, all that depends on how your cybersecurity incident response plan came out to be.
The optimization can be accompanied by a round of learning and training exercises to further fine-tune the process and maximize team efficiency.
Creating a cybersecurity incident response plan is the best defense mechanism
Having a CIRP can help your security team respond to incidents proactively and uniformly, thereby enhancing their incident response capability. All you need is the right resources, tools, and plan of action to decide the flow of work.
So, start building your cybersecurity incident response plan today!
