Shadow IT teams can have long-term positive impacts, but also short-term negative impacts.
Fifty-seven percent of small to midsize businesses (SMBs) have had high-impact “shadow IT” efforts occur outside the purview of their official IT department. Of that group, 85% currently have a shadow IT team operating in the business right now. Shadow IT efforts can range from low-impact incidents, such as an employee downloading a video conferencing tool that isn’t issued by the IT department, to high-impact ones, such as developing and deploying a new customer database outside the official IT environment.
Shadow IT teams often create cybersecurity threats and cost your business money. But they’re also nearly always creating something valuable. With the right approach and perspective, SMB leaders and IT project managers can make these rogue initiatives official, leveraging their insight while reducing risks.
We surveyed* 300 IT professionals and project managers at SMBs who have had high-impact shadow IT efforts affect their business in order to provide insight on this issue. We asked about why these teams form, the impact they have on operations and security, and strategies for managing and preventing their formation.
IT project managers hold a unique position, sitting between IT and “the business,” that allows them to be especially effective when leading the integration project as they can also help drive the culture changes needed to prevent the formation of new shadow IT teams.
/ Key findings
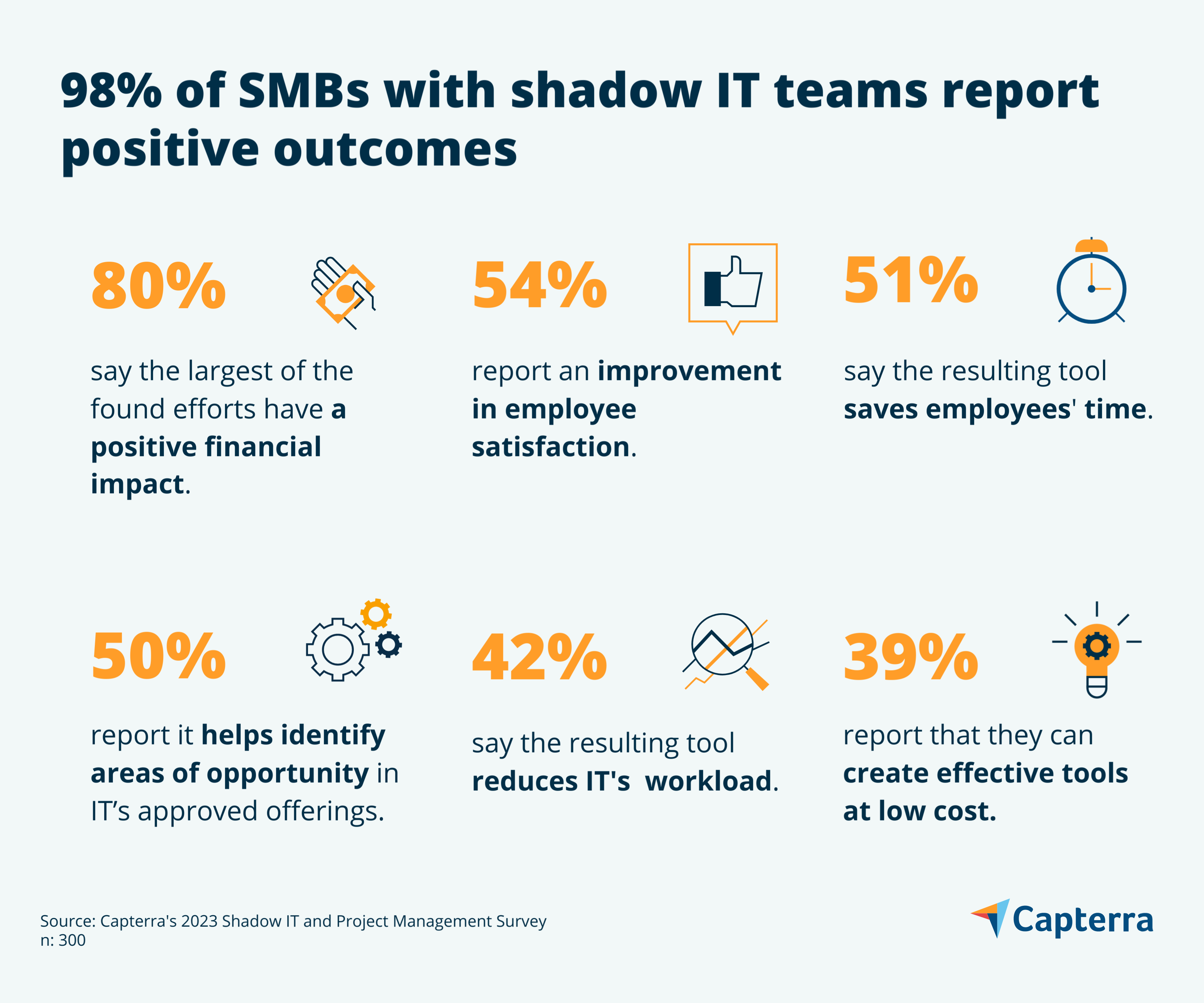
98% of SMBs who have had shadow IT teams report long-term positive impacts. The resulting effort:
Increases employee satisfaction (54%)
Saves employees’ time (51%)
Has a positive financial impact (80%)
There are short-term negative impacts, but could be mitigated with IT’s help:
89% of SMBs have had negative financial consequences, such as paying fines and replacing the created software.
76% of SMBs report the shadow IT effort found posed a moderate to severe cybersecurity threat to the business.
91% report challenges integrating the shadow IT work into their official environments, with reasons varying from the immense amount of time it takes, difficulty integrating with existing systems, and the cost being very expensive.
The solution? Education and embracement are keys to prevention. 94% report IT PMs will play an important part in preventing future efforts, along with employee education, updating company policies, and fostering a collaborative culture.
Shadow IT teams are rather common and create valuable tools to help employees work better, but they also bring unnecessary risks and can be costly. However, you can integrate their work safely while helping drive a culture of embracing and supporting shadow IT so the innovation stays, but the risks go.
What is shadow IT?
Shadow IT teams, also known as rogue IT teams, refer to employees who create and/or use technology and software without the knowledge or approval of the IT department. These teams often form in response to a perceived lack of support or resources from the official IT department and can have both positive and negative effects on the business.
Why do they form?
Half of SMBs who’ve found a shadow IT team within their company say that a lack of understanding/awareness of the correct process for getting new software/hardware is the top reason why the team is formed. The next most common reason is due to a perception that going through the IT department is too slow and/or cumbersome (41%), followed by the fact that an incubator team is created outside of IT’s awareness with a senior manager’s approval (37%), and then lastly, IT doesn’t respond quickly enough to the request for new software/hardware (35%).
What are they up to?
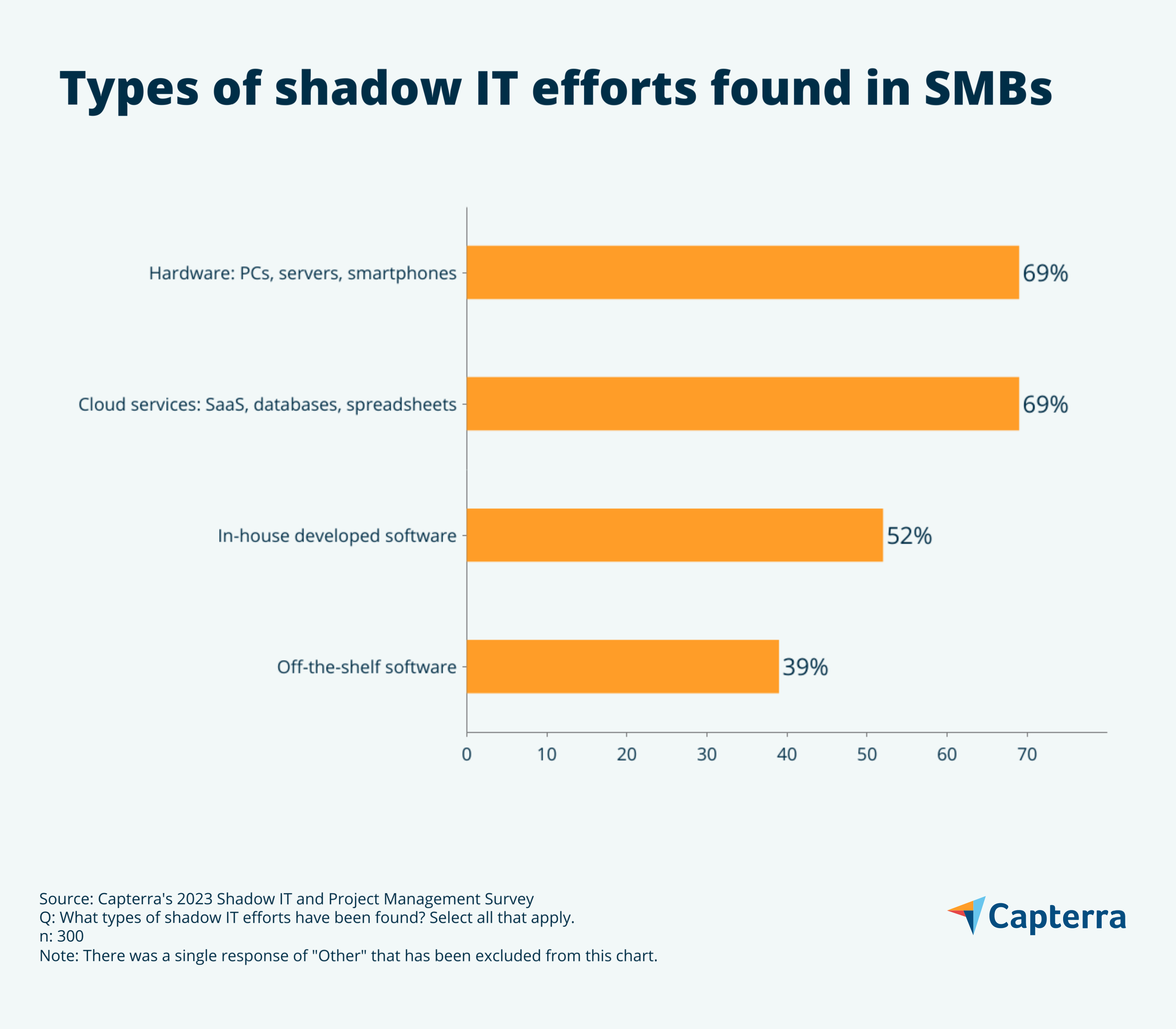
The nature and level of risk posed by shadow IT teams vary from rather mundane to extremely high risk. Adoption of new hardware and cloud services are the top most common types of shadow IT efforts found in our research, each having 69% of respondents experiencing it. Over half have found a full-blown software development effort happening outside of ITs purview.
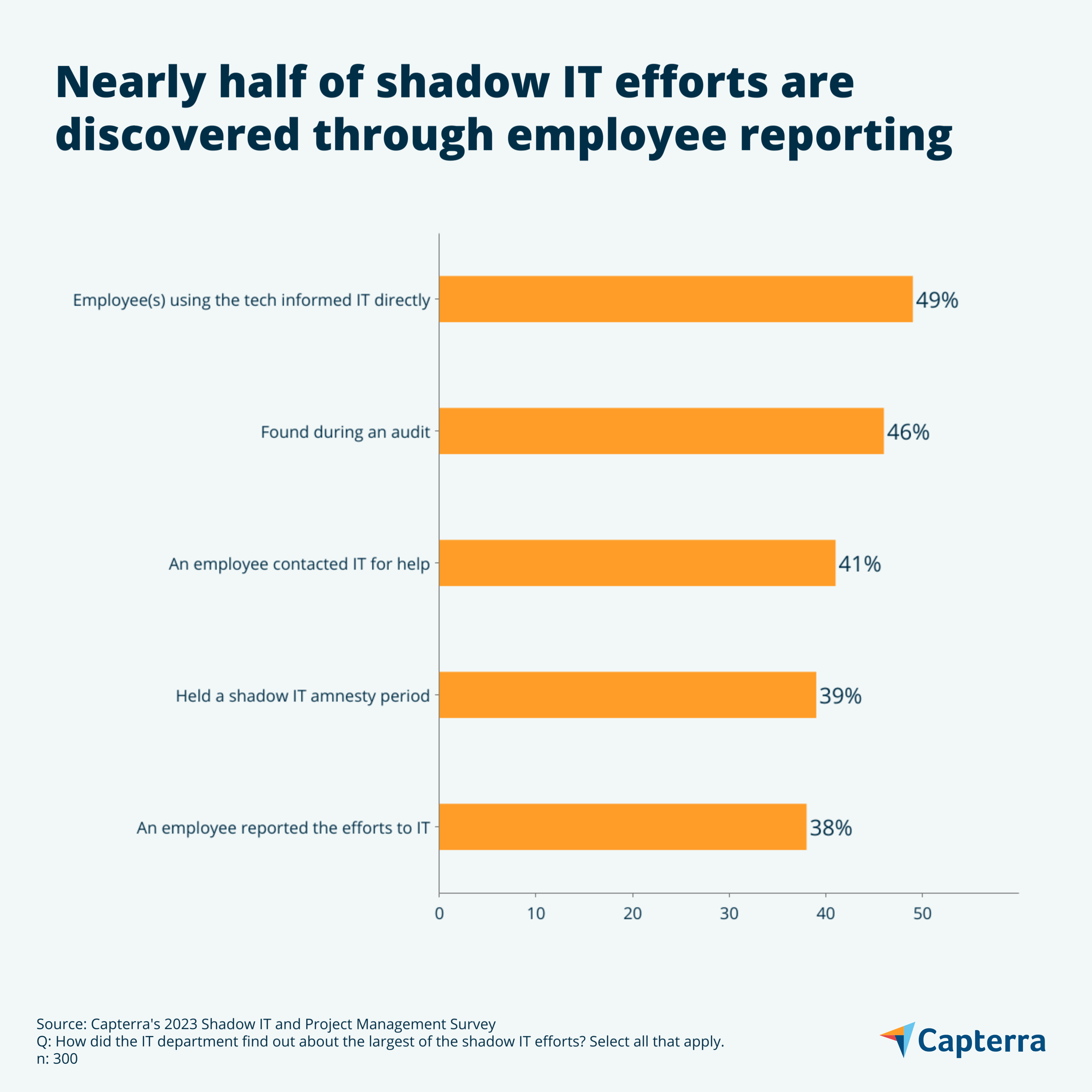
How do I find a shadow IT team?
Typically, you can find a shadow IT team by an employee reporting it or by performing an audit. When a shadow IT team creates a new tool and offers it to employees, those employees usually won’t even know the tool is an “unofficial” one and will eventually end up contacting IT about it. Our survey found that employees using the new tech will often directly inform the IT department of the existence of the tool (49%) and/or will ask IT for help using the tool (41%). Audits and amnesty periods are effective and proactive ways to find shadow IT teams at work as well.
Shadow IT efforts aren’t typically malicious and when found should be approached in a curious and supportive manner. Chastising employees who are trying to find better ways to get their work done will only send future efforts deeper into the corners of your business. This report will provide guidance for how you can find and safely integrate shadow IT teams into the official IT environment.
3 ways to incorporate shadow IT efforts into your business safely
Only 1% of SMBs report not working with the shadow IT team, and 4% immediately eliminate the work they create from the official environment. This makes sense when we also know that 98% of respondents said there was a positive outcome to the shadow IT effort they found.
These results indicate you should have a plan for how to incorporate the work of a shadow IT team if/when you find one, as it’s likely that their resulting work will prove effective by those using it.
Here are three approaches you can take to incorporate the work done by a shadow IT team:
1. Create an IT project with resources from both IT and the shadow IT team.
This approach has multiple benefits as it builds a relationship with both teams, the shadow IT team learns the official IT processes, and this is typically the quickest and most effective way to incorporate the work.
You should know:
This is the most popular way to incorporate the shadow IT team’s work with 37% of respondents using this approach.
2. The shadow IT team is instructed on how to integrate their work.
This approach works well if their work isn’t complex or requires integration with another system. But this approach doesn’t mean the team won’t need guidance or support from IT, so make sure the shadow IT team has a point of contact in IT to collaborate with as needed.
3. The IT department takes over control of the technology and performs the integration.
This approach may be the best option if the shadow IT team isn’t available to help in the incorporation of their work, but all efforts to get them involved should be explored prior to choosing this path. Not only will the integration run more smoothly with their help, but you won’t risk losing the spirit of innovation across the team.
You should know:
Our research shows about a quarter of the time the shadow IT team either isn’t willing to cooperate with IT or vice versa, senior leadership isn’t supportive of integrating their work, and/or the employees disengaged with the project after it was put under IT control.
Now that we’ve covered ways to incorporate the work of a shadow IT team after you’ve found it, let’s get into how you can prevent their formation going forward.
4 prevention actions you can take now
Whether you’ve already found a shadow IT team’s work or not, small-business owners and managers need to be aware of the potential formation of one and take proactive steps to prevent their formation. This can be achieved by updating existing IT policies and creating a culture that encourages open communication and collaboration between all departments.
Here are the most common prevention steps surveyed SMBs are taking to prevent future shadow IT teams from forming. You should consider if any of these would be appropriate for your business to incorporate too.
/ Steps to prevent shadow IT from forming
Increase cybersecurity: Install or update a company firewall, require approval for application downloads, and perform software audits regularly.
Update IT policies: Include directions for employees to request new tech and guidance for employees thinking of “going at it alone.” Adopt a lenient shadow IT policy to encourage innovation but with necessary guardrails to mitigate risks.
Create a “fast-track” project type: Offer shadow IT teams an alternative path with streamlined processes to help implement requests with IT’s guidance.
Provide employee training: Many employees may not be aware of the risks created by shadow IT efforts and need specific guidance on how to proceed safely. Make sure to also include directions for how to report shadow IT activity without fear of punishment.
Prevention steps should be taken on a regular basis along with fostering a collaborative culture with the IT department and non-IT tech-minded employees. Make updates to policies and procedures in transparent and fair ways to encourage teams to work together to build solutions for the business. This way you can minimize risks while benefiting from employee innovations.
Embrace the innovation to reduce risk
The research findings* indicate that while shadow IT teams can bring benefits, such as increased employee satisfaction and low-cost innovation, they also pose significant risks to the security and integrity of business operations.
In addition to fostering a culture of integration, SMB leaders should also consider implementing measures such as access control software and employee training programs to minimize the risks associated with shadow IT teams.
It's important to note that, with the right management and leadership, shadow IT teams can be beneficial for your business. Therefore, it's critical for SMB leaders to strike a balance between harnessing the potential benefits of shadow IT teams while minimizing the risks.
Survey demographics
For the deeply curious, here we’ve charted the business types and sizes data of our survey respondents.
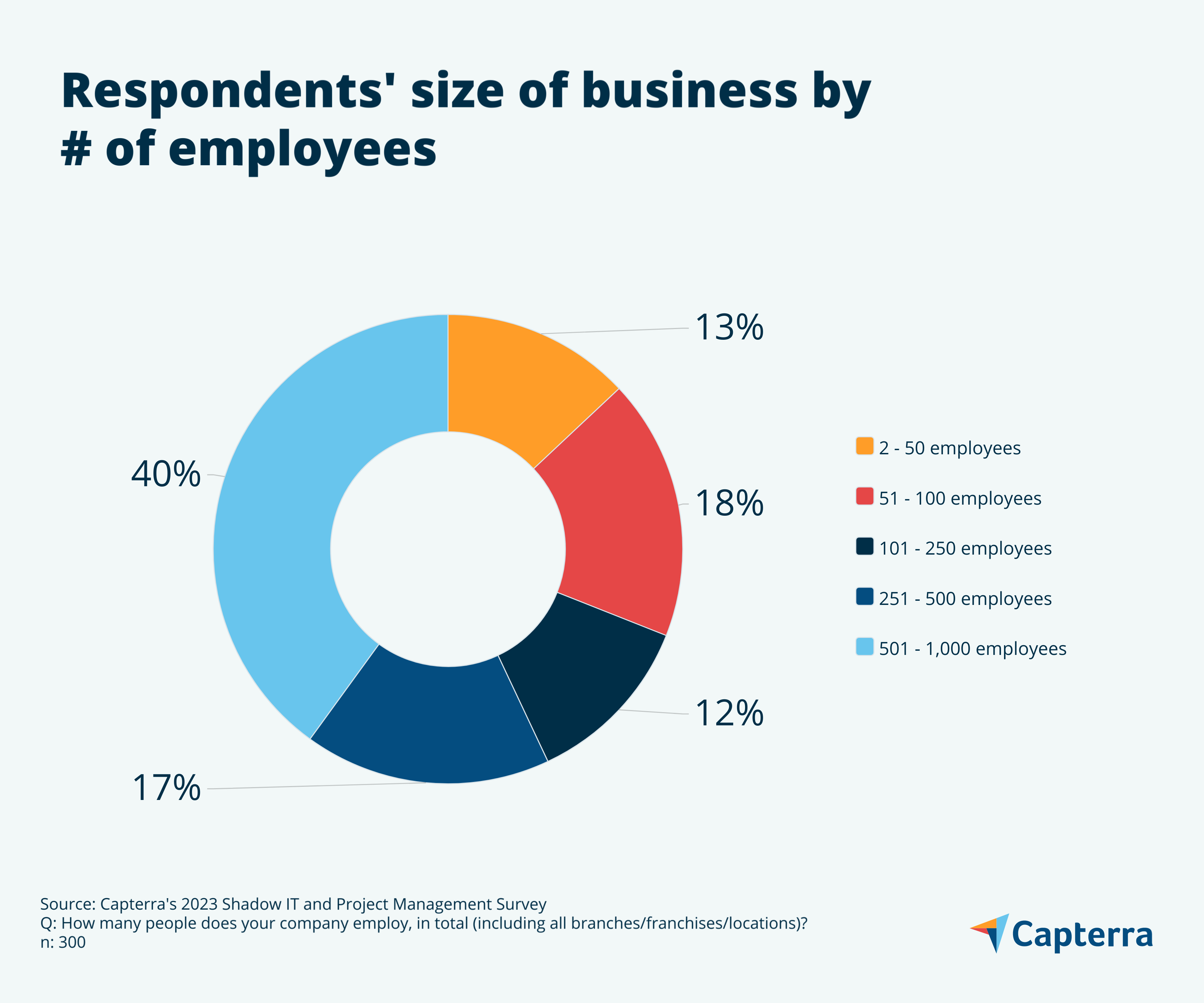
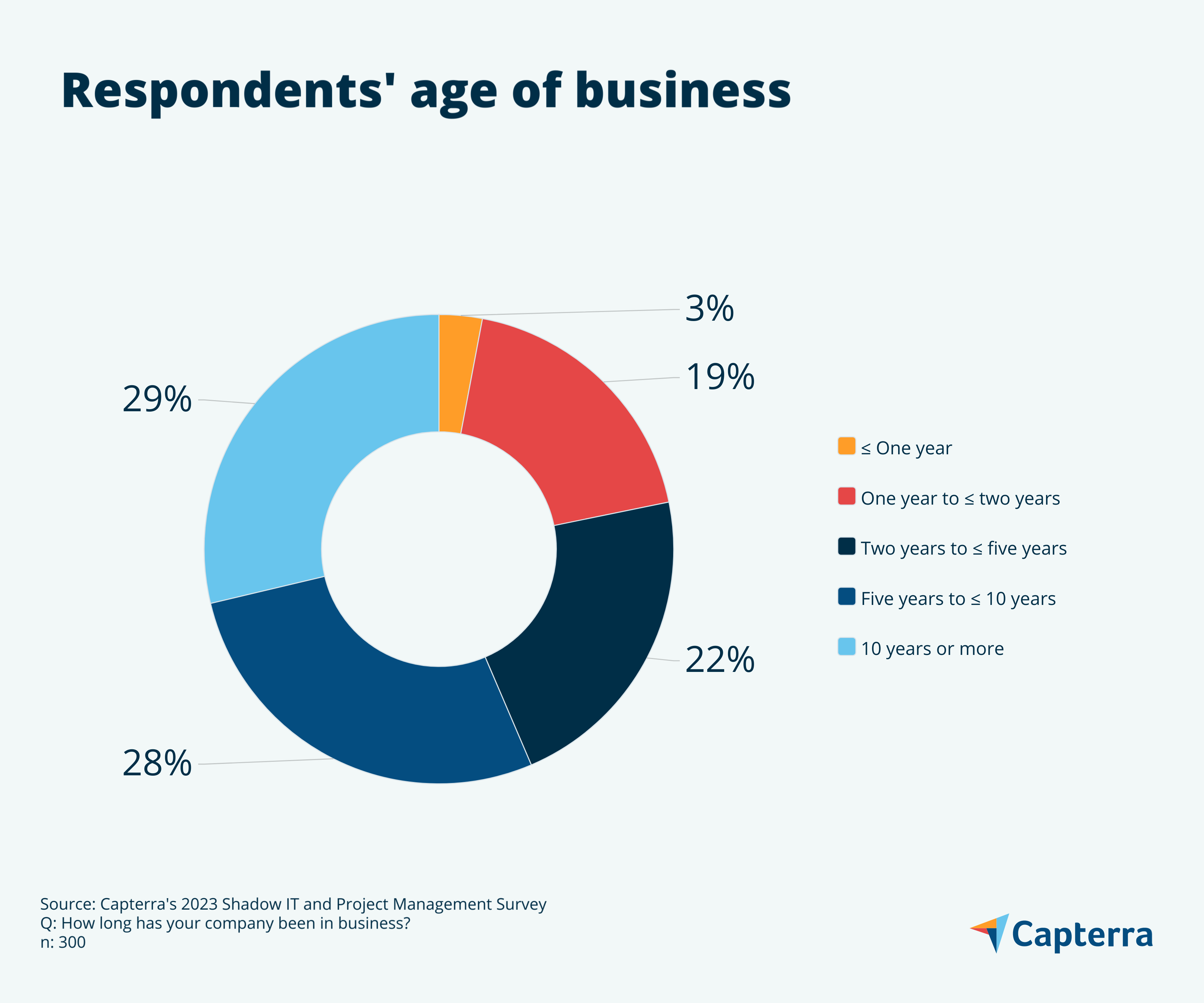
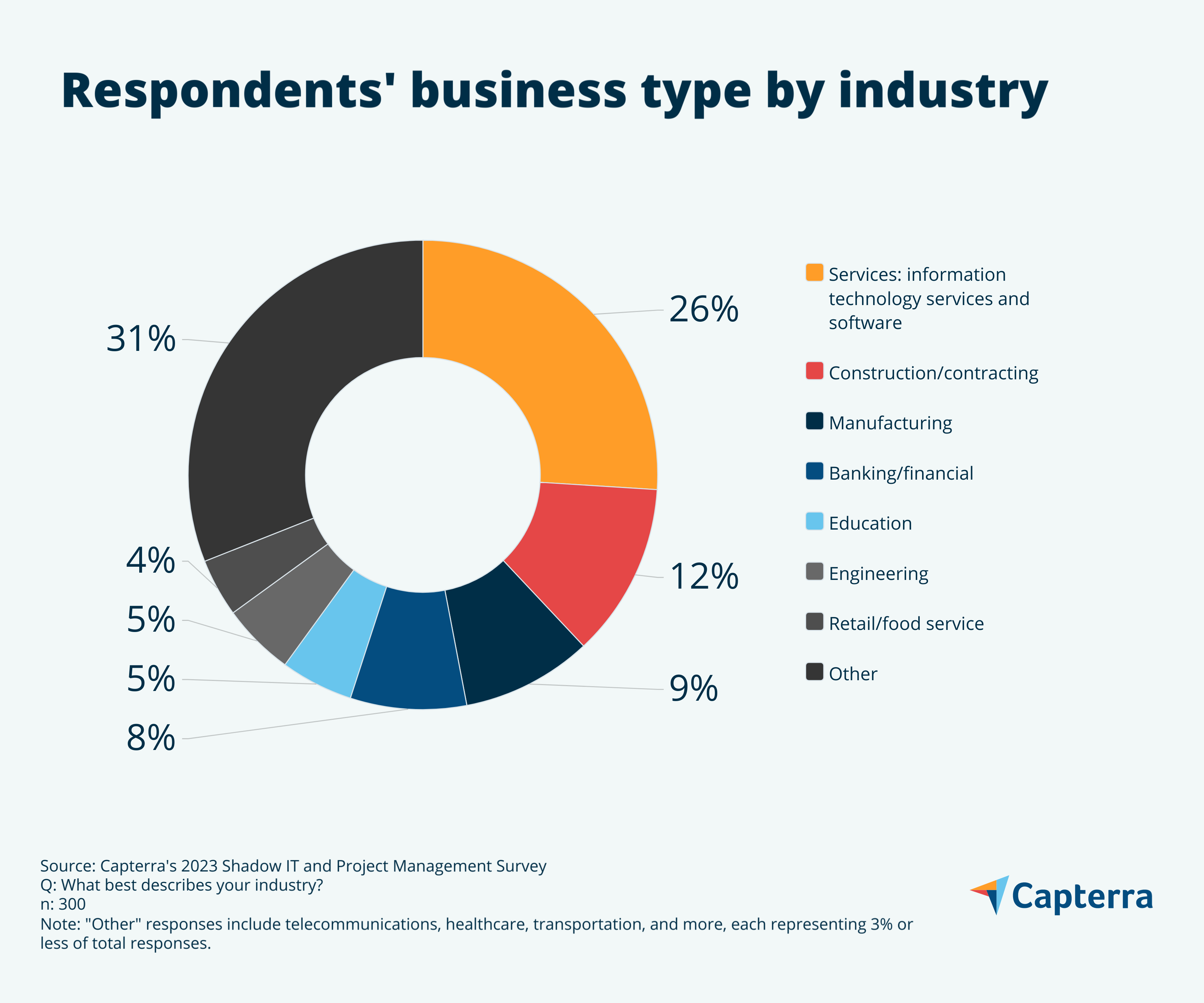
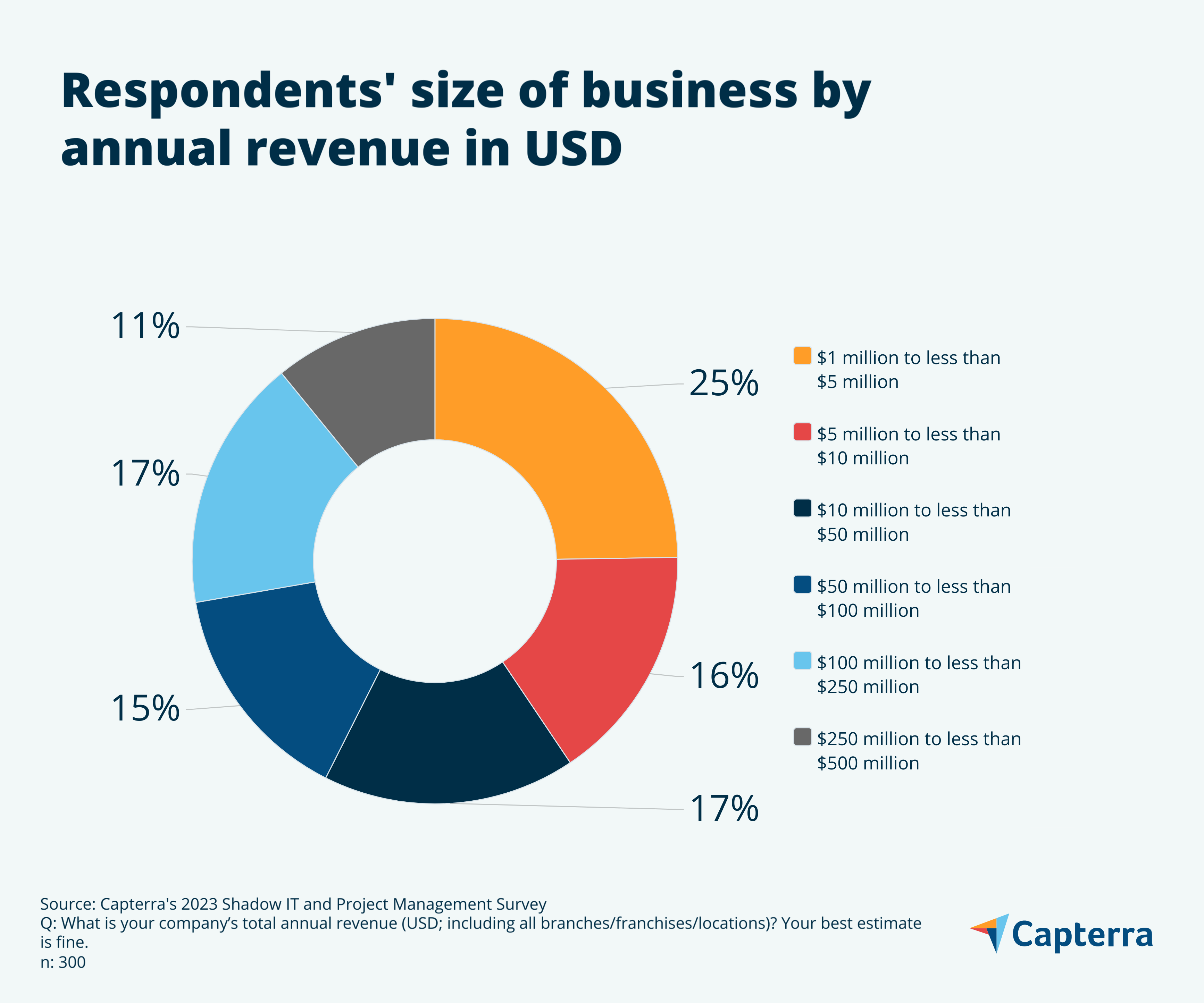
Note: All numbers have been rounded to the nearest whole number, and therefore all charts may not add up to 100%.
