Security features are deal breakers for most companies—nearly half have stopped using a software platform due to security concerns.
If you’re looking for new business software, chances are security is a major factor in your decision-making process. According to Capterra’s 2023 Security Features Survey*, half (50%) of all U.S. software buyers consider security as influential in the buying process—more than any other factor. Security also plays a factor in companies deciding to discontinue the use of software—nearly half (45%) have stopped using a specific software platform due to security concerns.
In this report, we’ll explore more of our survey findings and dig into the security features software buyers like yourself find most important so you can avoid wasting time and money on a product that doesn’t meet your needs.
/ Key findings
According to software buyers, security is the most influential factor (50%) when making a purchase, followed by functionality (49%) and ease of use (46%).
Nearly half (45%) of U.S. businesses have stopped using a software platform due to security concerns.
The most important security feature for software buyers is data backups (76%), followed by security alerts (72%) and encryption in transit (68%).
One in three (33%) software buyers are seeking passwordless authentication options.
A certification from the Cloud Security Alliance is the top choice for software buyers.

Security features are dealbreakers for most software buyers
According to buyers, security is the number one factor (50%) when making a software purchase, followed closely by functionality (49%) and ease of use (46%). Software pricing came in at number four at 38%. These results confirm that buyers are willing to pay a premium for a secure product that is intuitive and well-designed, elements that tend to go hand-in-hand.
It’s clear that software buyers have security features front of mind during the purchase process, but what exactly are they looking for? We asked which features they consider “must-have,” and more than any other, data backups are the biggest dealbreaker (76%). This makes sense in an era of rampant ransomware that makes data backups absolutely crucial.
Coming in second is the ability to receive security notifications (72%), followed by encryption in transit (68%), and encryption at rest (67%). While this is not an exhaustive list, it comprises many of the most significant security features a buyer might expect from a modern software platform.
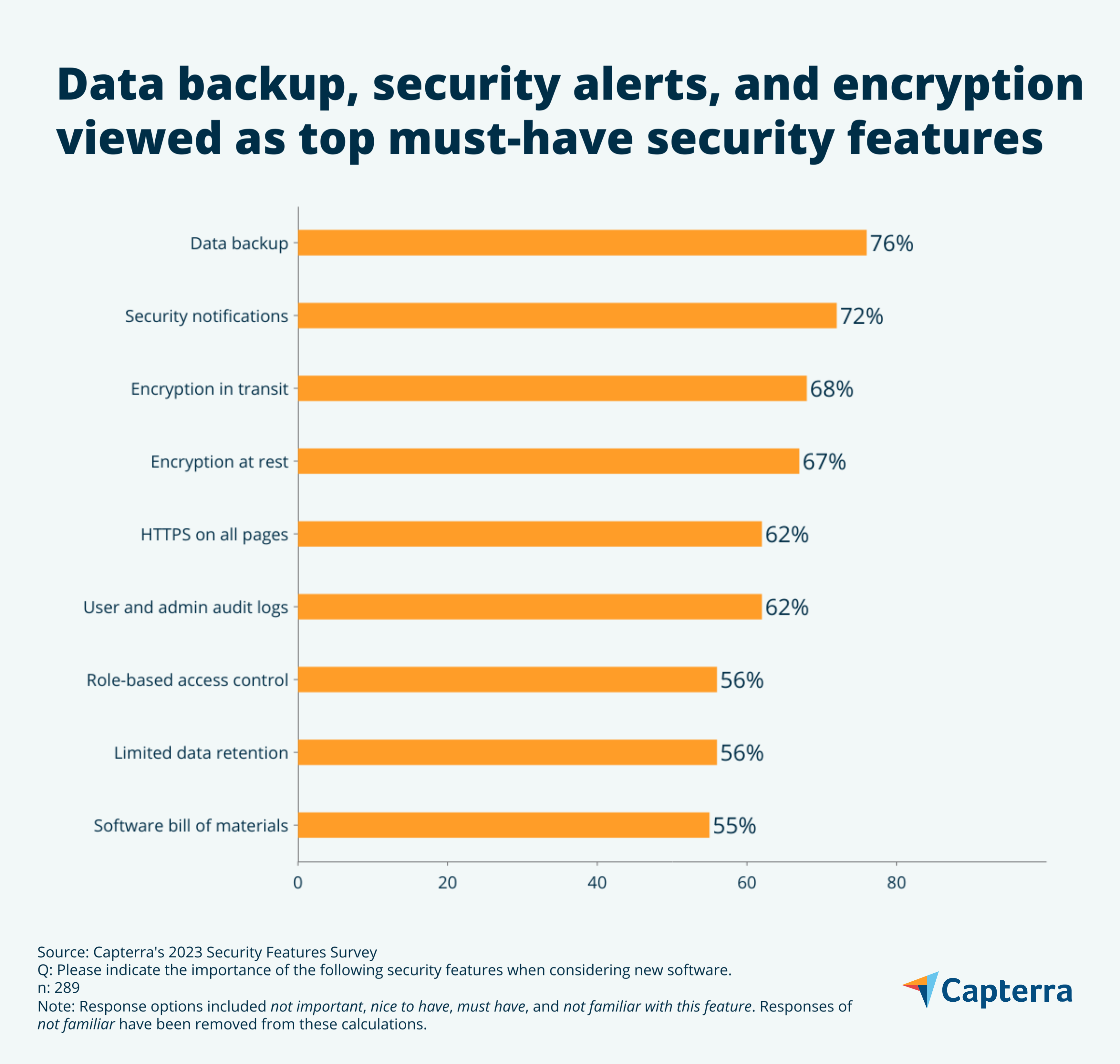
At the bottom of our list with a still respectable 55% is the availability of a software bill of materials (SBOM), an emerging feature that is likely to become more prevalent in the future.
What is a software bill of materials (SBOM)?
An SBOM is a structured list of metadata that identifies and tracks the components used to build a software package. SBOMs are meant to inform organizations about the code used to develop software so that security and compliance risks are better understood as they emerge. Many regulatory bodies in the U.S. and Europe have mandated SBOMs as a prerequisite for software vendors to do business with government agencies or regulated organizations.
In recent years, software supply chain attacks have increased as bad actors leverage (or create) vulnerabilities in one component to gain access to another until they reach the intended target. In fact, our 2022 Data Security Survey** found that one in three (33%) IT security managers were facing a software supply chain vulnerability.
Perhaps the best recent example of a software supply chain attack, the 2021 Log4j vulnerability impacted a pervasive open source logging tool used in countless applications and hundreds of millions of devices[1]. Due to Log4j’s ubiquitous nature, most organizations were left scrambling to determine whether their network was secure.
The Log4j situation exemplifies why SBOMs are key to unraveling the complex web of components, dependencies, and supply chain relationships used in modern software development. As software supply chain attacks continue to rise, so too will demand for SBOMs.
Buyers looking for robust authentication options to boost security
Strong authentication has never been more important in an age where passwords are commonly reused, cracked, or leaked on the dark web. We’ve covered the benefits and seeming inevitability of passwordless authentication in previous reports (see box below) but that much-more-secure future is still far away due to legacy (and even many new) software products that depend overwhelmingly on passwords for authentication.
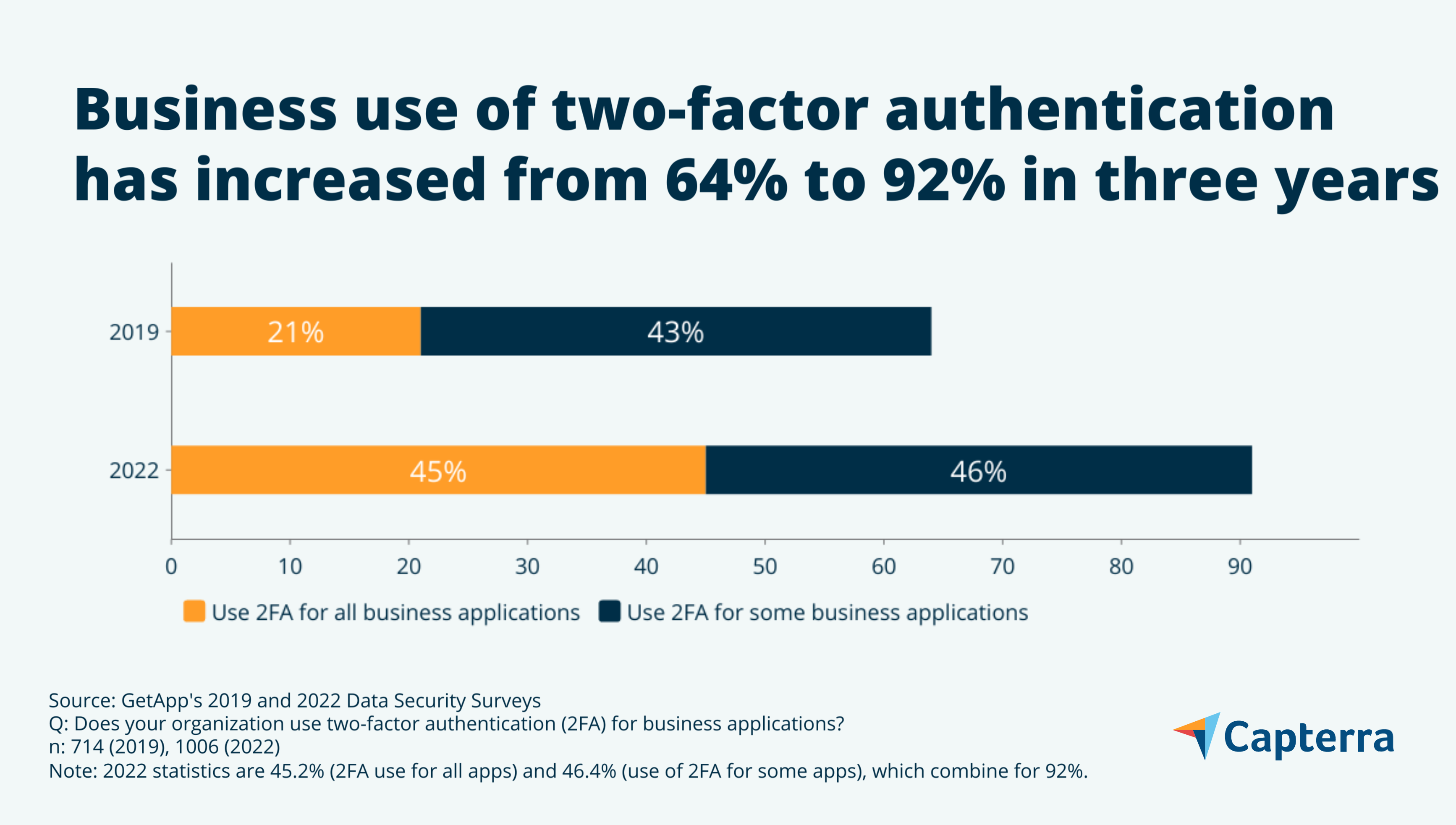
Fortunately, most companies now use two-factor authentication, which our research shows has grown from 64% in 2019 to 92% in 2022**. Even better, the percentage of companies that use it for all applications has more than doubled in the same time period.
Our latest research finds that software buyers are still looking for password authentication more than any other kind (59%)—but not by much. Nearly as many (52%) look for software token compatibility (e.g., DUO, Google Authenticator), 40% pursue hardware tokens (e.g., USB key), and 39% are eyeing biometric authentication (e.g., fingerprint or facial recognition).
One in three (33%) software buyers are actively looking for passwordless authentication options. A full one in four (28%) software buyers are interested in contextual/behavioral authentication, a method sometimes referred to as zero-factor authentication. This method depends on risk signals based on expected versus received data.
A well-known version of contextual authentication is the use of cardholder location by credit card companies to identify suspicious activity, but it can use anything from a person’s keystroke pressure to the way they walk (i.e., gait).
Read our recent report to learn more about passwordless authentication:
Certifications and attestations alleviate buyer concerns about software security
Security certifications and attestations by software vendors let you know that the tool you’re buying adheres to specific protections. We asked software buyers which security certifications or attestations would make a software vendor more appealing.
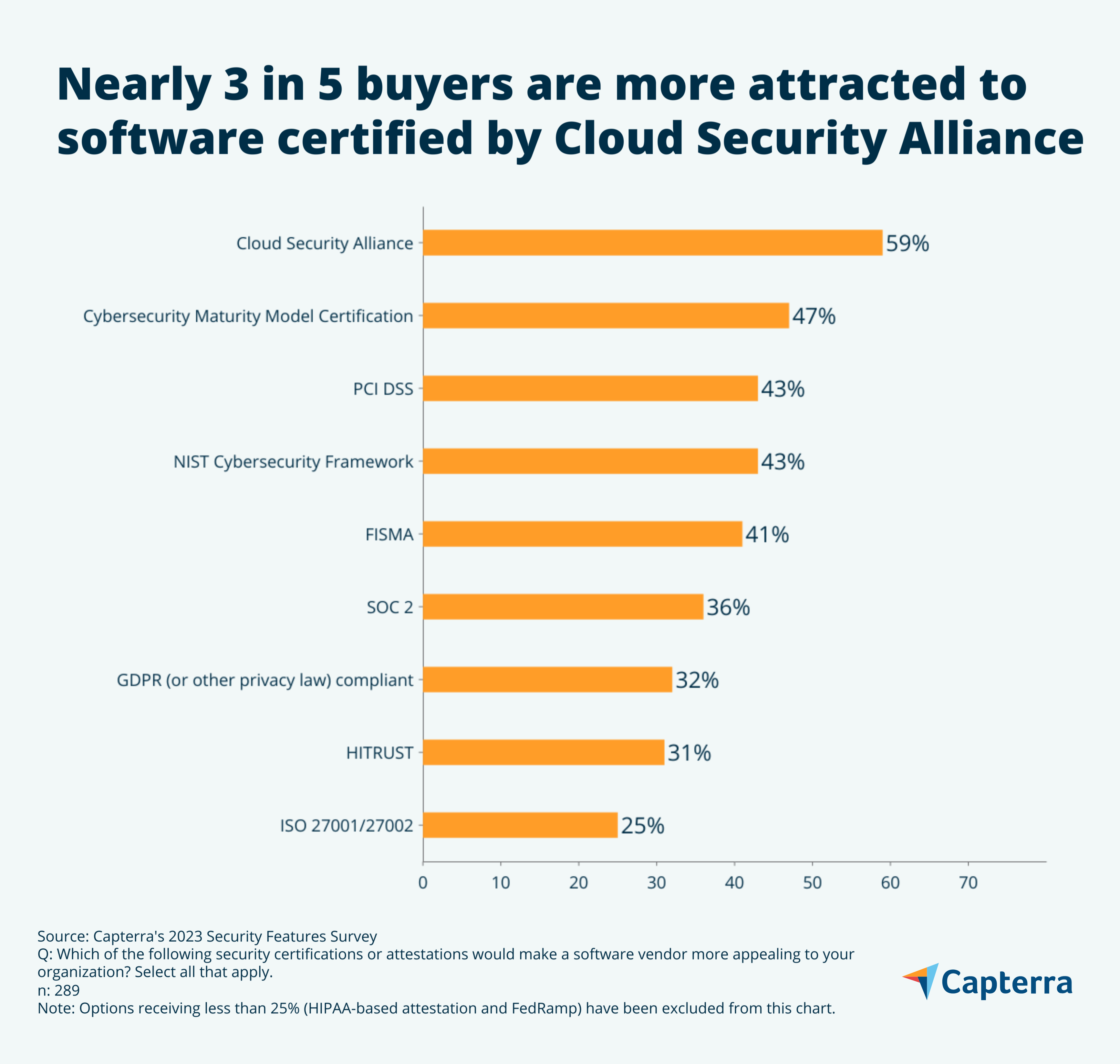
According to 59% of software buyers, a Cloud Security Alliance certification makes software more appealing, followed by the Cybersecurity Maturity Model Certification (CMMC) at 47%, and a tie for third with the Payment Card Industry Data Security Standard (PCI-DSS) and the NIST Cybersecurity Framework (NIST CSF), both at 43%.
Let’s take a look at our top three (or four in this case) most-wanted standards to better understand their appeal:
Cloud Security Alliance Certification: Certification by the Cloud Security Alliance helps cloud service providers prove that their platform is secure. Level 1 of the CSA’s Security, Trust, Assurance and Risk (STAR) certification offers several variations that require self-assessment. Level 2 STAR attestation or certification generally builds off other certifications such as SOC 2 or ISO 27001 and requires an independent third-party audit.
Cybersecurity Maturity Model Certification (CMMC): The CMMC comprises 18 domains and is designed to protect sensitive unclassified information that the U.S. Department of Defense (DoD) shares with contractors and subcontractors making it applicable to hundreds of thousands of companies. Certification requirements are being phased in over five years, taking full effect on January 1, 2026, and are tiered (Level 1, Level 2, etc.) according to the sensitivity of data shared.
Payment Card Industry Data Security Standard (PCI-DSS) Certification: The PCI-DSS certification is an industry-driven mandate applicable to any software vendor that uses credit card payments as part of its product’s workflow. The standard has 12 requirements that companies must meet to achieve certification. The process involves qualified security assessors (QSAs) who verify controls and document findings in a compliance report.
NIST Cybersecurity Framework (NIST CSF): The National Institute of Standards and Technology’s Cybersecurity Framework is a voluntary guidance that was initially developed to improve security for critical infrastructure in the U.S. but has since broadened its scope to assist all businesses seeking to improve their cybersecurity posture. The framework comprises multiple implementation tiers along with five main components: identify, protect, detect, respond, and recover. Compliance with NIST CSF makes it easier for organizations to then gain compliance with other frameworks such as PCI DSS or FISMA.
Cloud service providers face challenges to prove that their platforms are secure. At the same time cloud service buyers tend to be uncertain about how to evaluate a provider’s security posture. It makes sense, then, that a certification by the Cloud Security Alliance is by far the top choice of software buyers and is increasingly being adopted by vendors.
Takeaways for software buyers
Continue to put a premium on security as a key differentiator when evaluating new software.
Ensure that the software package you buy offers robust authentication options that will allow you to reduce dependence on passwords.
Check for crucial security features including data backups, encryption, and security alerts—but don’t overlook less well-known (but important) features such as audit logs, data retention policies, or the availability of an SBOM.
Take time to explore the various security certifications to better understand which vendors are best suited for your security needs.
Looking for software? Explore our catalog to find the best tool for your business.
