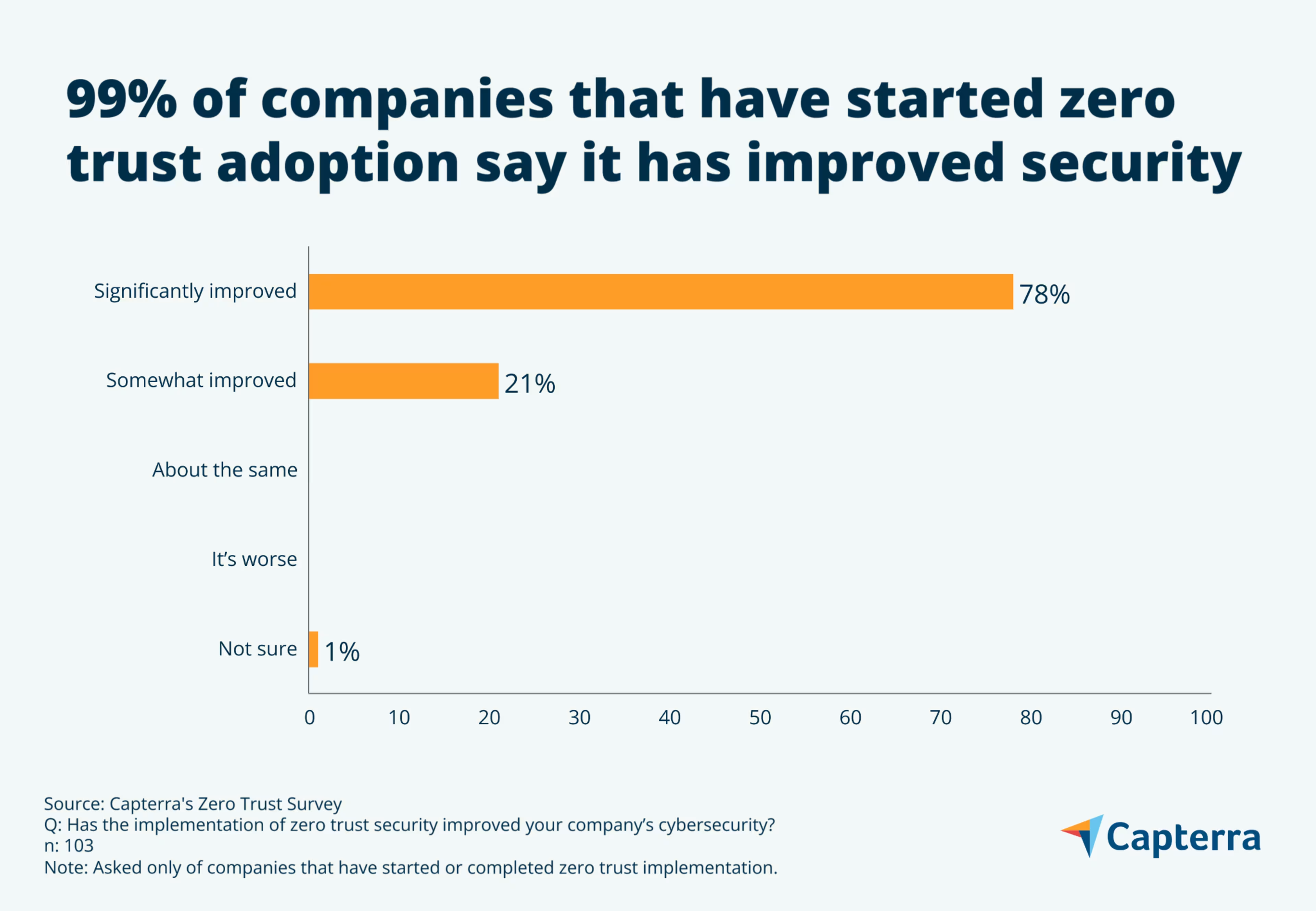
A near-unanimous 99% of those who have adopted zero trust say it has improved their company’s cybersecurity. Here’s what you need to know to start your company’s zero trust journey.
Zero trust is a security strategy—but it’s also a mindset. It doesn’t mean no trust, but it does mean no implicit trust. Clear? No? Okay, let’s dig into it.
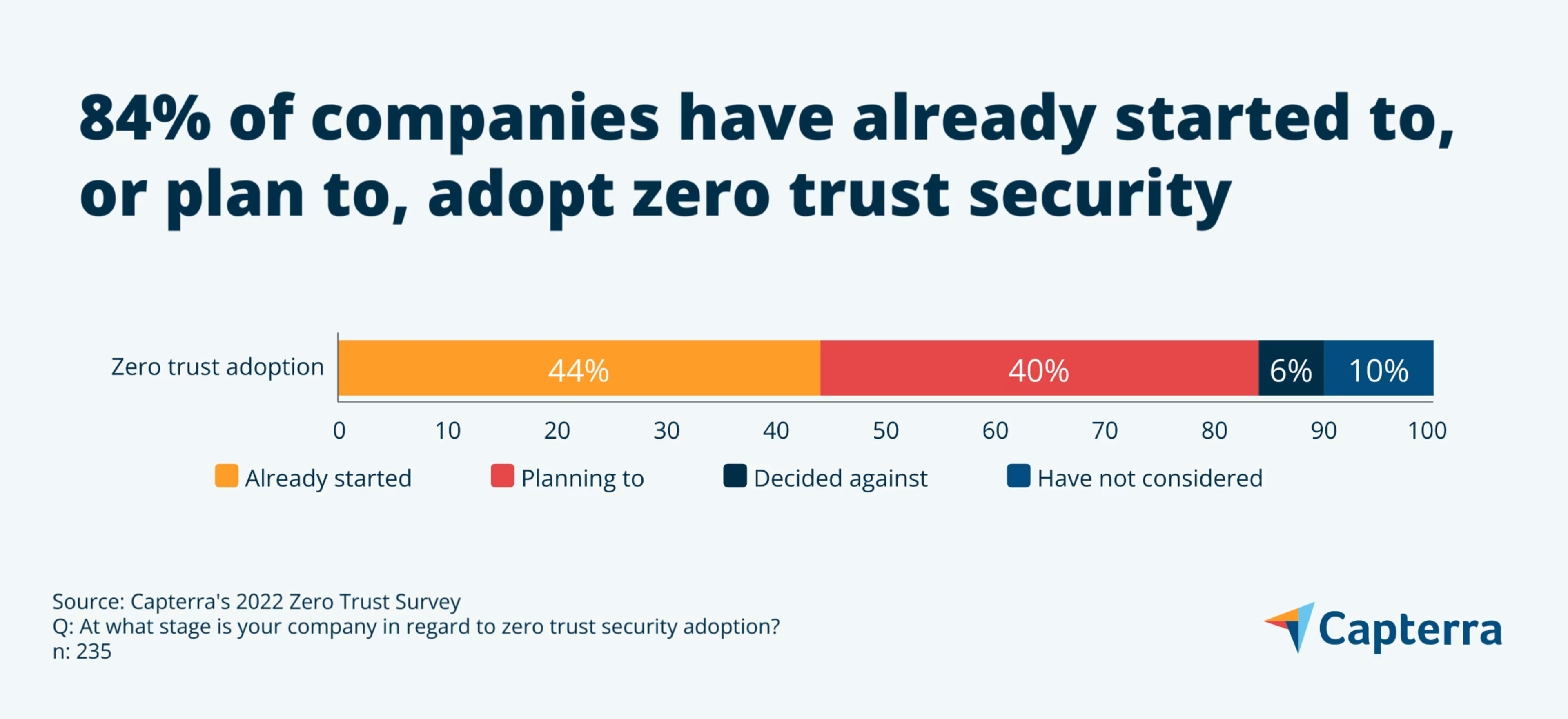
Our 2022 Zero Trust Survey[*] reveals that 84% of companies have decided to adopt zero trust strategies. If your company is concerned about growing security threats, read on to learn about the benefits of switching to zero trust, and how to deal with the challenges that come with it.
What is zero trust, and why do I keep hearing about it?
Zero trust is a strategy that makes it easier to optimize security for your business by explicitly identifying users and granting them just the right amount of access to your network.
Zero trust replaces implicit trust’s modest motto of “trust, but verify” with the merciless maxim “never trust, always verify.” If it sounds cynical, it should. Zero trust security operates under the mindset that a breach is either inevitable or has already occurred.
Accordingly, zero trust security serves as a direct replacement for implicit trust security, which historically has been the default for IT infrastructure. With implicit trust, once someone is inside of your security perimeter, you trust them implicitly without any further scrutiny. This strategy has proved inadequate for the modern targeted threat environment.

The security improvements of zero trust, which we’ll discuss below, are many and varied. Zero trust strategies are already recommended by organizations such as CISA[1] and NIST[2], and are now being mandated for federal agencies under President Biden’s Order on Improving the Nation’s Cybersecurity[3].
Further demonstrating the looming move toward zero trust, 44% of the companies we surveyed have already started zero trust implementation and another 40% plan to adopt it at some point in the future—only 16% have not considered or decided against it. Of those planning to adopt it in the future, 72% intend to begin implementation within the next year.
But despite the inevitable mass adoption of zero trust, our survey finds nearly half of the IT professionals we surveyed (47%) say their company’s leadership doesn’t understand zero trust security. Making matters worse, 40% of our respondents say they face challenges in obtaining the budget for new technology needed to implement zero trust security.
And while these issues might complicate your organization’s zero trust journey, you simply cannot maintain sufficient security using implicit trust security strategies in today's rapidly escalating threat environment.
What’s wrong with the security approach we’re already using (i.e., implicit trust)?
The implicit trust security model was designed for a bygone era and is no longer suitable for modern cybersecurity threats. In the past, when most work was done within a closed network with little connection to outside threats, a username and password seemed sufficient, and it was easy to assume that anyone operating within your security perimeter could be trusted.
Fast forward to today, and companies are connected to various Software-as-a-Service (SaaS) platforms, dependent on cloud-based data storage solutions, and increasingly hosting remote workers around the globe. In other words, security perimeters have expanded and attack surfaces have grown.
Moreover, cybersecurity threats themselves have shifted from generally passive malware infections to increasingly targeted and destructive attacks aimed at specific companies or individuals, often launched by highly-organized criminal organizations. For these reasons, companies need security strategies that continually verify identities and minimize potential attack impact.
So, is zero trust better than implicit trust? A near-unanimous 99% of those who have started or completed zero trust adoption say it has improved their company’s cybersecurity—78% say it has significantly improved cybersecurity.
What is the business value of zero trust?
Zero trust is designed to increase your IT infrastructure’s resiliency and reduce business disruption. This is important because our recent Ransomware Impacts Survey[**] found that the single biggest impact from an attack is on productivity with more than one in four attacks lasting longer than 24 hours (including 8% that last a week or longer). It's not surprising, then, that in ransomware attacks where the victim does not pay the ransom, one in three victims (34%) still incur more than $50,000 in losses.
Zero trust lessens the threat of cyber attacks such as ransomware by not only by preventing them in the first place but also by limiting their ability to move throughout your network if you are attacked. This is accomplished using strategies such as data classification, restricted access privileges, and network segmentation so that access to a part of your network doesn’t mean access to all of it.
Our research finds the top reason for zero trust adoption is to strengthen data security (72%), followed by a need to improve identity and access management (63%). Most cyberattacks involve compromised credentials or hacked passwords while a growing list of data privacy regulations have pushed businesses to strengthen data security practices, all of which is addressed by zero trust.
What’s more, the modern hybrid work environment needs to be flexible enough to support remote workers while preventing unauthorized access. Zero trust network access (ZTNA) supports remote work security by replacing vulnerable network technology such as VPNs.
What are the challenges of zero trust implementation?
According to our Zero Trust survey, restricting data access without impacting workflows is the top challenge faced by companies that have already implemented zero trust (49%), followed closely by developing new security policies (47%), and selecting zero trust vendors (46%). Let’s take a look at each of these.

Restricting data access without impacting workflows
When adopting zero trust, companies must ensure that employees, contractors, and business partners are able to access the data they need while restricting access to the data they don’t.
It’s important to recognize that removing access to previously available systems or data may cause frustration if handled haphazardly. That’s why zero trust must be a part of your company culture if it is to be successful. Employees should understand that zero trust does not mean they are not trusted and that it is simply intended to enable the business to succeed in the modern threat environment.
How to overcome it: It’s essential to identify the systems, devices, and users that access your network. From there, you can develop a strategy to map how data flows throughout your network and move to limit access to those who need it while denying access to everyone and everything else.
Developing new security policies
Zero trust typically requires the development of more extensive identity and access management policies along with granular network segmentation that adapts to specific workloads. Existing security controls are likely to be replaced little by little, both because of cost and a necessary transition period. Meanwhile, IT staff are often responsible for maintaining overlapping standards.
How to overcome it: If you’re unsure where to start, begin solving for a specific problem, such as improving identity management, by shifting to new controls that continually verify users based on role and behavior. Then, move to microsegmentation projects that securely connect identities to appropriate workloads (e.g., applications, containers, virtual machines).
Selecting zero trust vendors
Zero trust is a buzzword and has been added as a feature to countless software vendors' products. Right here on Capterra, our catalog features more than 1000 products that claim zero trust features. And while that may be, zero trust has clearly become a marketing tool as much as a security tool, further confusing its meaning and complicating the selection process.
How to overcome it: Selecting software is no easy task, especially when it involves fundamentally changing strategies. Use our strategies for selecting the right software for your company with our 5 Tactics to Increase Your Odds of a Great Software Match.
Zero trust is a journey, not a destination
Ransomware attacks, remote workers, and cloud-based everything are just a few of the reasons companies must begin planning their eventual transition to zero trust security. With that said, it’s unlikely that most companies will be able to fully transition to zero trust architecture any time soon—and that’s just fine. Any and all milestones your company hits on its journey toward zero trust makes it more secure.
Want to learn more about futureproofing your company’s security? Read our report Passwords Are the W0r$T!—It’s Time To Adopt Passwordless Authentication
