Keep ransomware attacks at bay by understanding how each type works.
Two in five (38%) small-business leaders have paid between $50,000 to $5,00,000 in ransom demand per our 2022 Ransomware Impact Survey*.

These extortion attacks come in various forms, and if your IT security team knows how each works to disrupt ongoing operations, they can plan proactive steps to tackle them.
We collaborated with Howard Globus[1], a cybersecurity evangelist and CEO of IT services firm IT On Demand, to dissect the five main types of ransomware—covering their impact, frequency, and prevention.
“Small businesses are like candy to these extortionists, especially after generative AI’s availability to the general public. It’s high time to understand how these attacks work. You never know who’s prying on your business and how high you are on their hit list.”


Howard Globus
CEO of IT On Demand
Globus also shared how to use artificial intelligence in cybersecurity to level up your small business cyber defenses.
1. Locker ransomware
Imagine you’re about to start your day at your small business. You turn on your computer and can’t access anything. Your mouse won’t move, your keyboard doesn’t respond, and a message demanding payment is on your screen. This is locker ransomware in action. It locks the victim’s computer system, including hardware access.
Attack process
Globus explains that the hacker inserts the malware, often disguised as a legitimate file or link, into your company’s network. The malware exploits vulnerabilities in your systems, such as outdated software that hasn’t been patched or a weak password that’s easy to crack. This lets the hacker control your system’s interface and lock you out instantly. It’s like a padlock on your computer, and only the hacker has the key.
Business impact
“You’re not dealing with stolen or encrypted files,” Globus clarifies, “but the catch is you’re locked out of your day-to-day operations. The disruption alone can bleed you financially, even if your data isn’t directly at risk. The costs come from the downtime, recovery efforts, and the potential hit to your reputation.”

Attack frequency
Globus says locker ransomware has a lower chance of occurrence today than the other types of ransomware. But our survey* results found that 15% of businesses experienced ransomware attacks last year (2022) due to unpatched software applications.
Tips to prevent locker ransomware
Here’s what Globus suggests:
Have endpoint protection in place. It can detect and block malicious software and unauthorized access attempts. Endpoint ransomware protection is multilayered and comprises antivirus/antimalware software, network and computer-based firewalls, and intrusion detection/prevention tools to alert on intrusions.
Update and patch your systems. Ask your admin to update all operating systems, software apps, and hardware firmware with the most recent patches.
Develop an employee security training program to educate all end users on phishing and social engineering scams. Train your employees to follow security best practices, such as not opening unsolicited attachments or clicking on suspicious links. Fifty-three percent* of businesses conduct security awareness training at least once every six months.
2. Crypto ransomware
Unlike the locker type, crypto ransomware doesn’t just lock you out of your systems—it scrambles your data into unreadable gibberish. It encrypts your files, client details, and work documents and asks for a ransom payment to provide the decryption key.
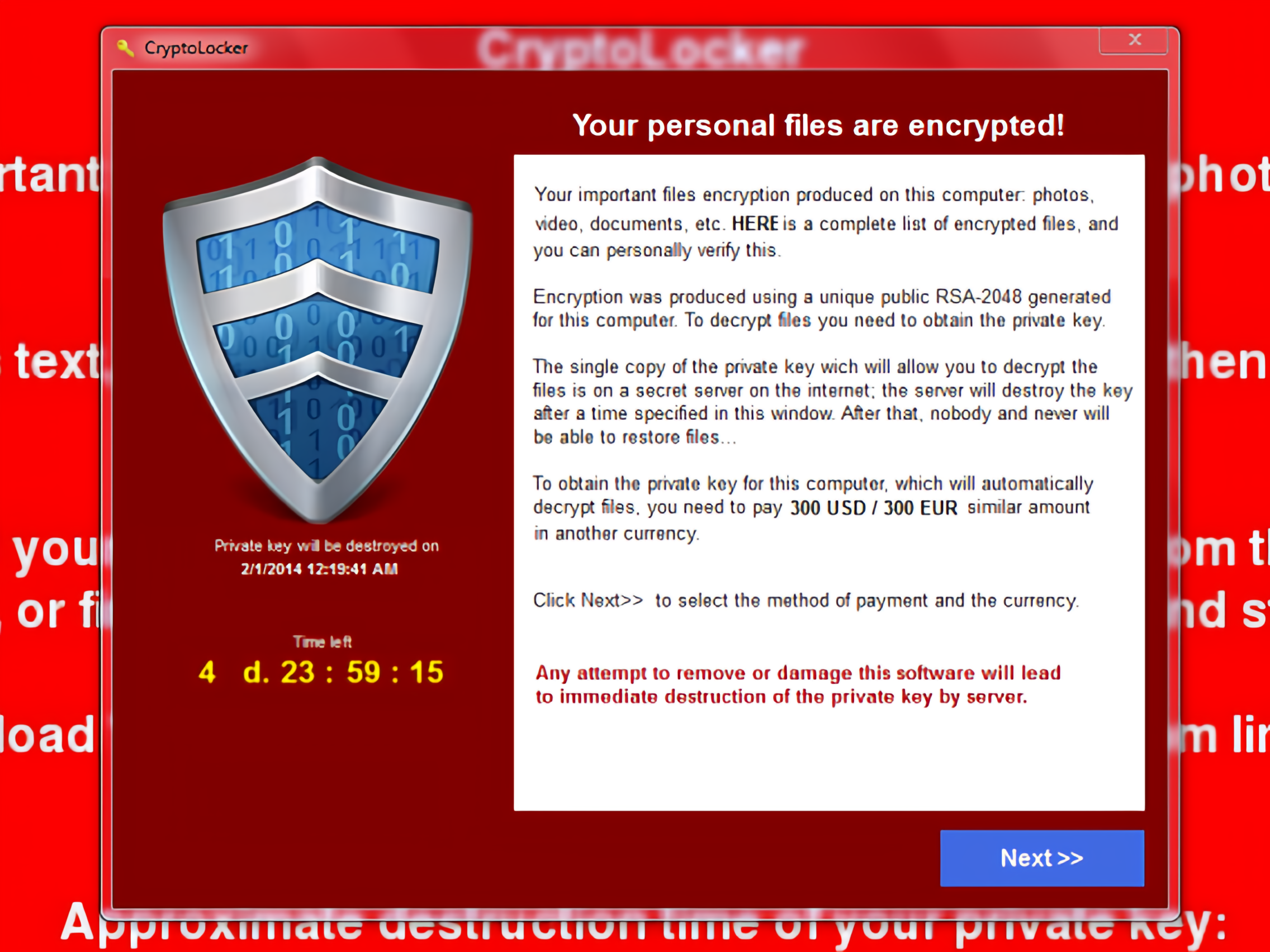
An example of a crypto ransomware message[2]
Attack process
Globus says, “Crypto ransomware is a bit more advanced. The hacker infiltrates your system, often through a malicious email attachment or a compromised website. The malware they insert is even capable of evading detection by antivirus software. Once inside, this malware spreads to other systems on your network and encrypts files.”
More than half (56%) of business leaders in our survey* report malicious file attachments or links in phishing emails as the top reason for ransomware attacks on their businesses.
Business impact
Globus calls crypto ransomware a double whammy. You can’t access your data because it’s encrypted, and the financial fallout can be even more severe. You’re looking at stalled operations, recovery costs, and possibly even a ransom payment. You might lose that data forever if you don’t have a sound backup system.

Attack frequency
Globus highlights crypto ransomware as the most common type we see. He warns: “Small and midsize businesses (SMBs) get hit the hardest because they often lack robust backup systems and continuity plans.”
Tips to prevent crypto ransomware
Globus recommends having these measures in place:
Regularly back up data on all systems, and have a recovery plan in place. Ensure your backups are stored offline or in cloud storage. Test the backup data regularly to ensure it’s usable and can be accessed.
Implement network segmentation to isolate critical systems and data from the rest of the network. This practice helps contain the spread of ransomware injection and limit the impact of the ransomware attack.
Adopt the least privileged access principle. Give your staff access to only those resources that they need to perform daily tasks, and assign administrative access on a need basis only. This approach minimizes the risk of an accidental user-triggered attack.
Narrow your search for IT services with our list of companies in the following areas:
3. Doxware
Also known as leakware, this threat actor doesn’t just steal your data; it even threatens to expose your secrets. Picture this: Your client details, internal communications, or even trade secrets plastered on some high-traffic corner of the internet.
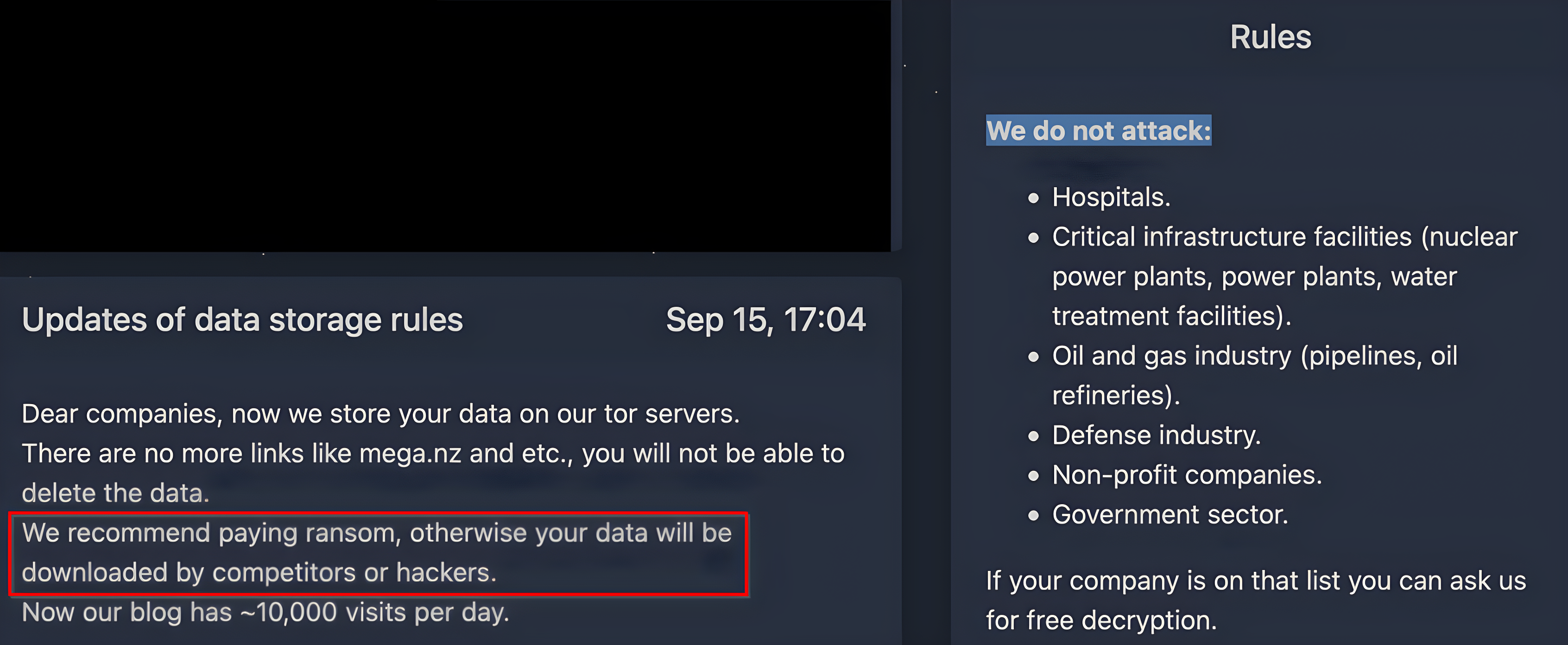
An example of leakware ransomware[3]
Attack process
Globus says, “Doxware is a bit different. It allows the hacker to infiltrate your system through phishing emails and exploit software vulnerabilities. Once inside, they copy your sensitive data. Sometimes, these hackers even use ransomware messages to distract you while copying your business files.”
Business impact
“Doxware is like a digital blackmailer,” Globus explains. “It holds your sensitive information hostage and threatens to spill it to the world. The risk level can range from medium to extremely high, depending on what information the ransomware attacker gets their hands on.”
Imagine the fallout if customer data, proprietary information, or political secrets get leaked. You could face fines, legal action, and costs for credit repair and monitoring for affected customers. The reputational damage alone can hit your bottom line hard.

Attack frequency
Globus says doxware is less common than crypto ransomware, but he also reports an alarming trend: “We’re seeing an uptick in doxware attacks. SMBs are particularly vulnerable because they often lack robust data loss prevention measures.
“Moreover, cybercriminals can extract data quietly, without arousing suspicion, and ransom it multiple times. This means that even though doxware attacks may not be as frequent as other types of ransomware, their impact can be felt multiple times over a longer period. Once your data is out there, you can never be sure it’s truly been destroyed. It’s the gift that keeps on taking.”
Tips to prevent doxware
Globus advises using these measures:
Segment your data using labels to designate importance and sensitivity. Then, use access control and encryption for sensitive information to reduce the chances of unauthorized access or exposure of data.
Implement data loss prevention (DLP) software. DLP tools can monitor and prevent ransomware attacks, including doxware, from transmitting or modifying your data.
Develop and use an employee security training program (as explained before).
4. Double and triple extortion ransomware
Double and triple extortion ransomware attacks are like two sides of the same dark coin. With double extortion, you’re already dealing with encrypted files and data exposure threats if the ransom isn’t paid. But triple extortion takes it further by hitting your network, customers, and partners with distributed denial-of-service (DDoS) attacks in which your company’s website is knocked offline.
Attack process
Globus says, “In double and triple extortion attacks, the ransomware attackers first infiltrate your system, often through phishing emails or by exploiting software vulnerabilities, and sometimes even remote desktop protocol vulnerability. After they encrypt your files, just like crypto ransomware, they copy your sensitive data and threaten to expose it if you don’t pay up.
Then, they launch a DDoS attack that floods your systems with excessive traffic from multiple sources, often using a botnet, which is a compromised computer network. This overwhelms your systems, making them inaccessible. It’s like they’ve created a traffic jam blocking all your customers from reaching you. The goal is to increase the pressure on you to pay the ransom quickly.”
Business impact
The data risk in both cases is exceptionally high. Your files are encrypted, your data is at risk of being exposed, and your network faces the threat of relentless DDoS attacks. The potential financial damage is staggering, affecting your business, customers, and partners.
Legal liabilities, regulatory penalties, reputational damage, incident response costs, lawsuits, and the never-ending monitoring of customers and partners—all these factors contribute to the financial toll of these attacks. Triple extortion amplifies these consequences due to the added complexity and scale.

Attack frequency
“While these attacks are less common than others, the alarming rise in their usage is a cause for concern,” Globus says. “SMBs often find themselves unprepared to handle the magnitude of such attacks. The reputational damage and sheer work required to restore normal operations can be overwhelming.”

Tips to prevent double and triple extortion attacks
Globus recommends having these checks in place:
Regularly back up data on all systems, test the data to check whether it’s usable and accessible, and have a data recovery plan in place.
Use multilayered security measures, which involve a combination of security solutions (e.g., firewalls, extended detection systems, bot detection software, email security tools) to mitigate and protect against initial intrusion attempts.
Implement robust network security measures, and review alerts and logs for signs of intrusion or suspicious activities. Similarly, use website security software to monitor any unusual behavior or potential threats on your website.
Create, test, and update your incident response plan. This will reduce downtime and ensure a recovery process is available to implement immediately. Our 2022 Data Security Survey** shows that nearly 78% of businesses have a formal cybersecurity incident response plan.
Deploy DDoS mitigation solutions, including specialized hardware or cloud-based DDoS protection software, to detect and mitigate DDoS attacks in real time.
Regularly monitor and assess network capacity to ensure your enterprise network can accommodate sudden increases in traffic during DDoS attacks.
5. Scareware
Scareware is not your typical harmful malware but is still a ransomware variant with a crafty way of playing mind games. Globus compares scareware to a wolf in sheep’s clothing. It disguises itself as a helpful solution, preying on your fears and vulnerabilities.
You might encounter a pop-up window claiming your computer is infected with a virus, accompanied by an urgent message asking you to take immediate action. But beware, this is where the trap is set.
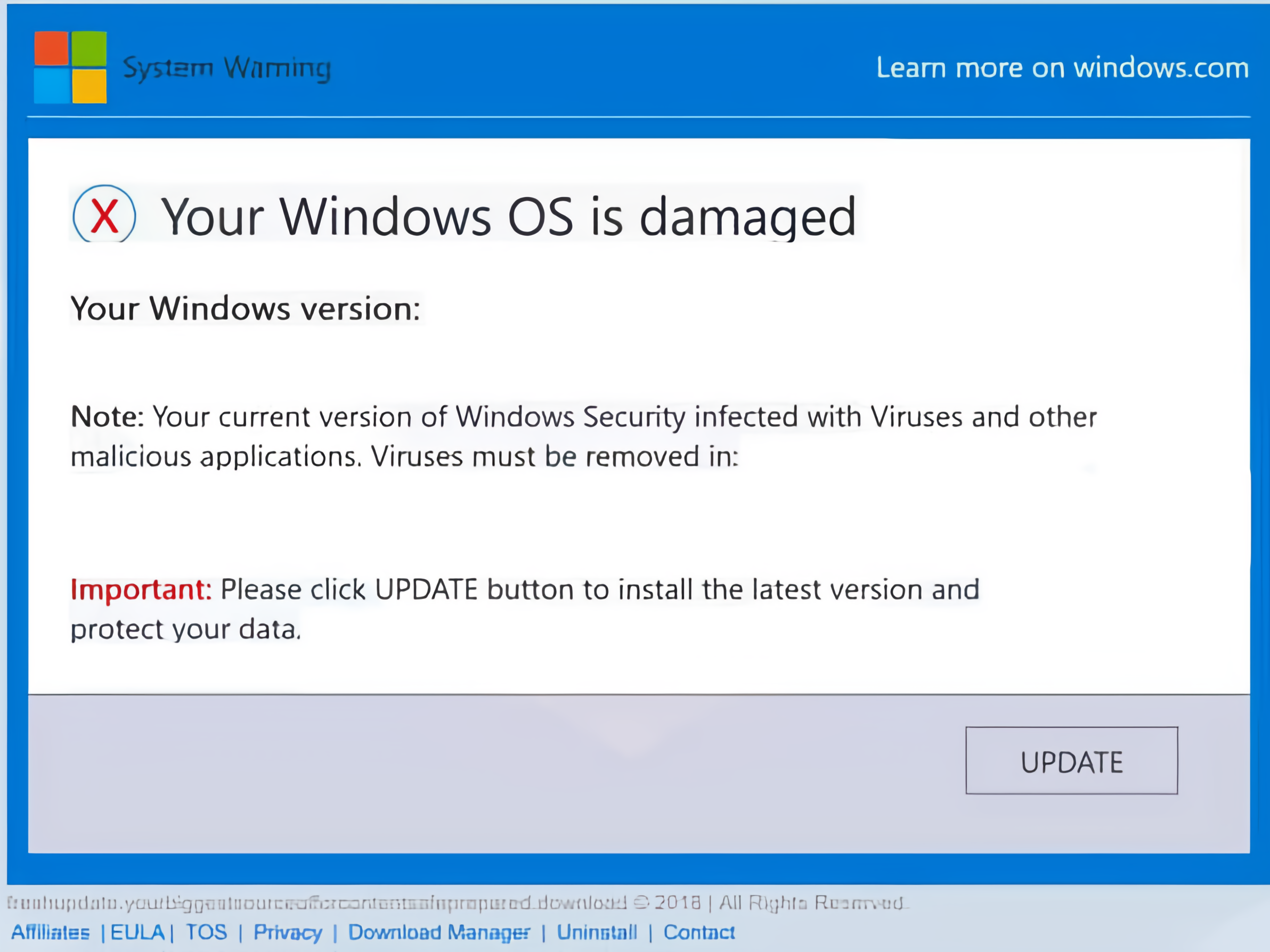
An example of a fake pop-up message in scareware ransomware[4]
Attack process
The hacker creates a fake warning message or phony antivirus software that pops up ads, fake websites, or even phishing attack emails to trick you into downloading the scareware.
When you see the warning or the software, you think you’re dealing with a virus or a problem on your computer. But when you click on the message or download the software to “fix” the problem, you install ransomware on your system.
Business impact
The data risk level may not be as high as in other types of ransomware since scareware doesn’t directly target your files or encrypt your data. However, falling for the scareware trap can have financial repercussions.
“Scareware can disrupt your operations, leading to lost productivity and missed opportunities,” warns Globus. “While it may not result in permanent data loss, the financial damage can still be significant, especially if you don’t have proper backups.”

Attack frequency
Scareware occurs more commonly than we know. Try visiting an illegal or compromised website to download a pirated movie or game, and it will be there to say “hello.” Not a significant figure, but 8% of small-business leaders* report their employees visiting compromised websites as the reason for a ransomware attack on their business.
Tips to prevent scareware
Globus says these checks can help prevent scareware:
Install a trusted antivirus to detect and block scareware.
Update your operating system and all software apps regularly. Updates often include patches for security vulnerabilities that scareware could exploit.
Always verify the source before clicking links or downloading any software. It probably is scareware if a pop-up or email seems suspicious or too good to be true.
Use a virtual private network (VPN) as an extra layer of security. It encrypts your internet connection and hides your IP address, making it harder for scareware to target you.
/ What is RaaS? Is it also a type of ransomware?
Ransomware-as-a-Service (RaaS) isn’t a cyberattack. Globus explains that it’s a business model in which hackers create and sell platforms that enable people with little to no hacking skills to launch ransomware threat attacks, typically against competitors. The providers of these platforms charge a fee for this service and often take a cut of any ransom collected.
The financial damage from RaaS can be substantial, especially if the person using it has inside knowledge of the business. Globus notes that RaaS has become increasingly popular, with many individuals targeting startups and new websites for financial gain.
Ransomware is evolving, and so should your security measures
Gartner[5] emphasizes that ransomware attacks are shifting from automated to human-led campaigns, targeting whole organizations rather than just individuals. Even Globus stresses that these attacks are becoming increasingly sophisticated.
The research-based expert tips we’ve provided aim to help you successfully prevent and combat different ransomware variants. But what’s most important is that you have a strong cybersecurity mechanism and use a variety of methods to keep ransomware threats at bay.
Confused where to start? Use these resources to get up to speed:

