In this report, we define and compare computer security and cybersecurity software to help you decide which one aligns with your business goals.
Given the constant risk of cyberattacks, computer security and cybersecurity have become crucial for businesses of all sizes, especially those dealing with sensitive and valuable data. While cybersecurity professionals can help businesses prevent digital attacks, they face a number of issues while preventing insider threats, handling data breaches due to remote work, meeting compliance mandates, and securing confidential data. Investing in computer security and cybersecurity software solutions can help them address these issues efficiently. But, how do you know which one to choose?
Computer security software and cybersecurity software are often mistaken for each other because both platforms protect critical IT infrastructure from malicious attacks. While the two tools do have some overlapping features, they are distinct in functionality. It is important to understand the differences between the two and their specific features in order to invest in the best solution for your business needs.
In this article, we'll talk about the similarities and differences between the computer security and cybersecurity software categories. We have also alphabetically listed the top five products for each category, based on verified software reviews. Read more.
What is computer security software?
Computer security software is a solution designed for protecting networks and computers from malware, threats, and unauthorized usage. The platform automates workflows, such as network management and incident reporting across networks, endpoints, and applications.
Computer security solutions can primarily be used to restrict and regulate access to sensitive information or computers. The software scans an organization’s computer network to identify potential vulnerabilities. It offers network security, antivirus, endpoint security, and virtual private network (VPN) functionalities to users. Additionally, the system offers real-time reporting and security alerts on network security issues, such as viruses and phishing attacks.
Narrow your search for IT services agencies with our list of companies in the following areas:
Key features of computer security software
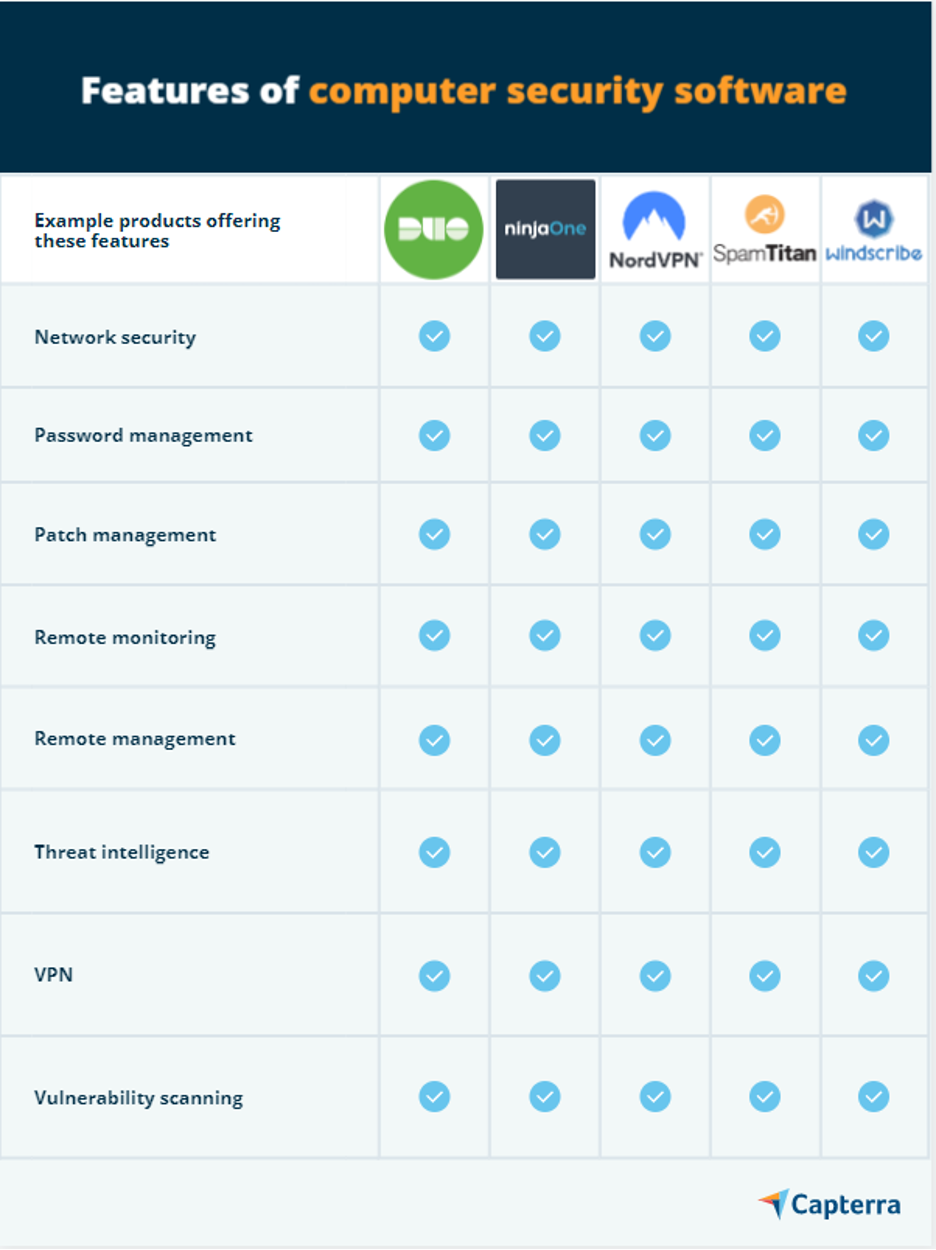
Typical features of computer security software include:
Data security: Offers security measures, such as authentication and encryption to safeguard sensitive information and prevent data loss.
Real-time monitoring: Provides real-time visibility into network systems that allow users to identify issues in application performance, prevent malicious activities, and improve incident response time.
Threat intelligence: Processes and analyzes threat data to identify existing or emerging threats, understand the nature of attacks, and enable network security teams to prevent these attacks.
Antivirus: Detects, prevents, and removes viruses from a computer system.
Endpoint protection: Secures a network’s endpoints, such as desktops and laptops from threats.
Network security: Prevents and monitors unauthorized access, misuse, or modifications in a computer network and network-accessible resources. The system also offers virus, ransomware, and identity theft protection to users.
Password management: Stores and manages passwords in an encrypted database to ensure confidentiality and prevent unauthorized access. The system also assists users in retrieving lost or forgotten passwords.
Patch management: Tests, identifies, and updates missing software patches across a variety of endpoints, including computers and servers.
Remote monitoring and management: Monitors client applications, networks, and endpoints remotely.
VPN: Extends virtual private network over public networks to enable protected information exchange.
Vulnerability scanning: Monitors applications and networks to identify, analyze, and report security vulnerabilities.
Top 5 computer security software
These five products are listed in alphabetical order (see the end of this piece for the full methodology for how these products were chosen).
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
What is cybersecurity software?
Cybersecurity software leverages machine learning and artificial intelligence technologies to secure critical IT resources against emerging cybersecurity threats. The software protects businesses from digital attacks, including unauthorized data access, identity thefts, and potential system vulnerabilities, such as viruses and ransomware. It also allows users to take the backup of critical business data to ensure business continuity in the event of a cyberattack.
Cybersecurity tools can be used to protect an organization’s computers, servers, networks, and data. There are different subsets of cybersecurity, which include application security, network security, and information security.

Key features of cybersecurity software
Typical features of cybersecurity software include:
Activity monitoring: Monitors and records user activity on computer systems and networks. The tool also provides activity alerts to report any illegal, fraudulent, or any other undesirable user behavior.
Endpoint protection: Monitors and protects endpoints, such as desktops and laptops, against cybersecurity threats. The system enforces security policies across endpoints to detect and respond to intrusions and malware.
Threat response: Identifies malicious behavior in real time and offers immediate remediation to security threats.
Antivirus: Identifies and removes software viruses, such as trojans, adware, and worms from a computer system.
Data security: Protects confidential data across all applications and platforms from unauthorized access and corruption.
DDoS protection: Monitors incoming traffic and protects network resources against distributed denial of service (DDoS) attacks.
Firewalls: Secures data and trusted networks by preventing unwanted traffic from accessing the operating system.
Policy management: Defines and implements rules and procedures that help safeguard critical IT assets and resources.
Reporting and statistics: Generates customizable reports, such as events, sessions, activity time, security failures, and audit reports among others.
Top 5 cybersecurity software
These five products are listed in alphabetical order (see the end of this piece for the full methodology for how these products were chosen.)
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
Trial/Free Version
- Free Trial
- Free Version
Device compatibility
Screenshots
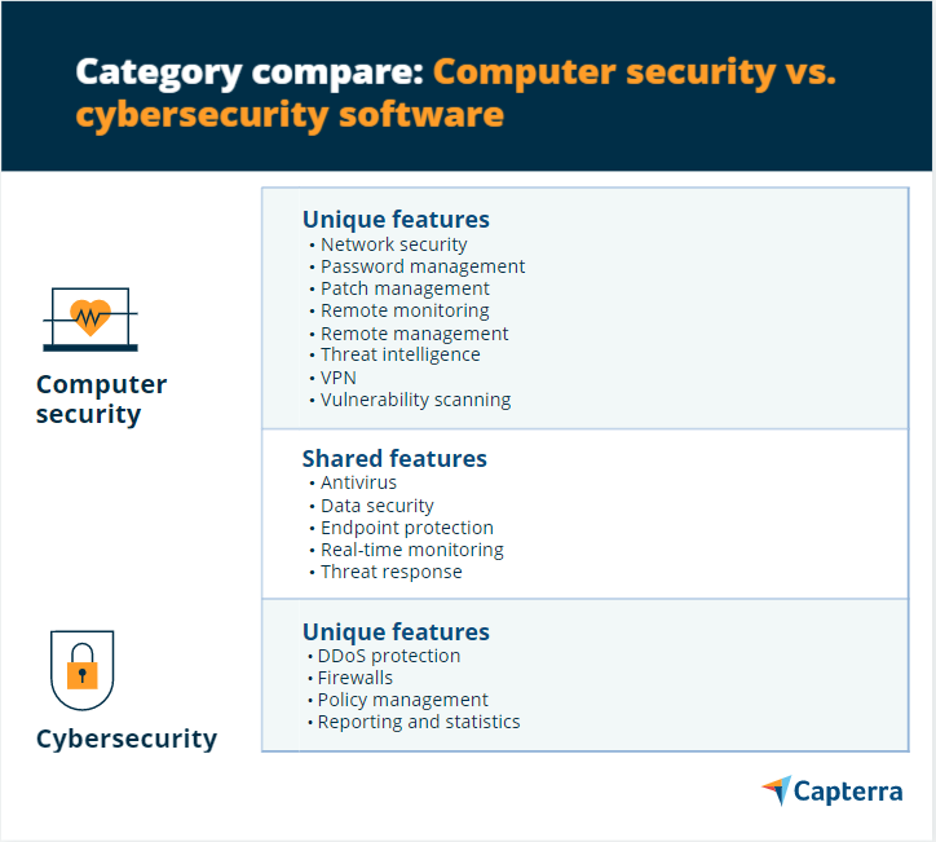
What do they have in common?
Computer security is an important subset of cybersecurity. Since both these platforms have a lot in common, the two software solutions are often used interchangeably. Talking about the similarities between computer security and cybersecurity solutions, both these tools:
are used to protect virtual data from viruses, breaches, hackers, leaks, phishing attacks, malware, ransomware, and other digital threats and malicious activities.
involve processing system updates and patching to prevent IT vulnerabilities and threats.
facilitate remote or real-time activity monitoring.
Some of the common features of computer security and cybersecurity software include activity monitoring, threat response, antivirus efforts, and data security.
Which security software is right for your business?
Before investing in computer security or cybersecurity software solutions, make sure to assess your business’s security requirements and objectives.
Cybersecurity software provides data protection and IT security on a larger scale. Therefore, the tool can be used to ensure both physical and network security. The software aims to secure physical devices of the organization, including laptops and monitors from external threats, such as malware, data hackers, and external ransomware threats .
Computer security software, on the other hand, is more limited to ensuring the safety of physical assets and devices. Unlike cybersecurity solutions, computer security software safeguards assets from internal threats, such as theft or unauthorized access. The software enables users to protect the confidentiality, integrity, and accessibility of devices.
If you are a small business owner with a team of IT professionals or someone from the network security team who is majorly looking to safeguard physical IT assets, you may want a computer security solution. However, if you are a cybersecurity professional, such as a cybersecurity analyst, looking to protect physical devices and virtual data stored in networks, clouds, and servers against cyberattacks and malware, investing in a cybersecurity solution would be a better idea.
Once you’ve decided which software to use, head to our computer security software and cybersecurity software category pages where you can find a sortable list of products and software reviews from verified users.
If you want to narrow down your search to only the most popular and highest-rated solutions, visit Capterra’s Shortlist reports for the top computer security software and cybersecurity software tools—our reports are based on an analysis of thousands of user reviews.
How to choose the best security software for your business
Shortlisting the right security software for your business can be challenging, especially with so many given options in the market. Here are some considerations that you can keep in mind while evaluating the best security systems for your needs.
Assess real-time monitoring capabilities: Real-time monitoring is important for identifying security threats and system vulnerabilities. The best computer security or cybersecurity solutions are capable of monitoring networks and devices in real time and conducting vulnerability scans to prevent digital attacks. The software should also provide security alerts and offer real-time analytics about critical IT events, such as user permission changes, configuration-related issues, and failed/unknown login attempts.
Consider software scalability: Before you invest in a security software solution, make sure that the system is able to support your growing business dynamics with minimal cost impact. Select a security tool that is capable of adapting to rapidly evolving IT needs and safeguarding your systems from potential threats, even in the event of an increase/decrease in the data load.
Look for remote monitoring functionality: Remote monitoring of devices and networks keeps IT professionals alarmed about system vulnerabilities, failures, and potential system issues. Before you finalize the best security software for your business, make sure that the tool allows IT service providers to monitor devices, networks, servers, and endpoints, even from remote locations. This will help them detect issues, such as data breaches, misconfigurations, and missing software patches before they escalate into something critical.
Common questions to ask while selecting the best security software for your business
Here are some questions that you can ask the software providers before selecting the best security software for your business.
Does the software offer multi-layered security?
A multi-layered security framework is essential to counter all sorts of flaws and threats in your computer system. Select a software solution that offers multiple security controls, such as firewalls, antivirus, patch management, and malware scanners to identify and prevent threats more effectively.
What are the available password management features?
Password protection is the first step towards protecting sensitive data and computer devices from hackers and malicious activities. Make sure that the security software you select offers necessary features, such as a password generator, multi-factor authentication, role-based permissions, and end-to-end encryption for managing important credentials.
What are the customer support options?
Live chat support is critical for computer and cybersecurity professionals. While the majority of issues can be solved easily, you may want a live agent on the other side of the line to help you address a quick concern. Before investing in a security solution for your business, make sure that it offers multiple communication options, including phone, email, and live chat. You can also look out for local language support to ensure proper communication.










